Recommended Blogs
Why Cyber Security has become a Boardroom Discussion

The year 2020 was full of challenges with rapid lockdowns in different countries across the globe and this year 2021 also seems to be no better than the last year. Typically, when the world began coping up with the COVID-19 pandemic blues, a wave of cyber-attacks continues to shake the world of businesses across domains.
Table of Content:
1. Latest cyber-attacks across industries during 2020-2021
2. Various dominant types of cyber-attacks in recent times
3. The emerging need for different types of security testing
4. Why today’s CXOs should leverage security testing?
5. How we can help with your security testing assessments?
6. Benefits of VAPT
Earlier this month, on April 04, 2021, 533 million Facebook users’ phone numbers and personal data have been leaked online according to ‘Business Insider’ report!
These cyber-attacks pose a great risk to the identity and security of data of not only the general public but also the government and other institutions, and the cost of breaches has been consistently rising in recent years. This has also raised the dominance of new cyber vulnerabilities that emerged from shifting to a remote workforce with more IT employees shifting towards ‘WFH.’
This new work culture has truly expanded the cyber-attack surface and added many vulnerabilities for hackers to exploit from home offices too. Some of the other major reasons for these continued cyber-attacks are remote working, extensive cloud breaches, pandemic-related phishing, ransomware attacks, social engineering attacks along with more cyber threats on Internet-of-things (IoT), etc.
Today, invariably, board members, directors, and CXOs continue to review their organization’s risk practices to include network breaches and failures in their business continuity planning to safeguard from possible cyber risks and other similar incidents to stakeholders.
There had been nearly 445 million attacks detected since the beginning of 2020. There have been many types of cyber-attacks in recent times across industries which have been detailed below.
Latest cyber-attacks across industries during 2020-2021
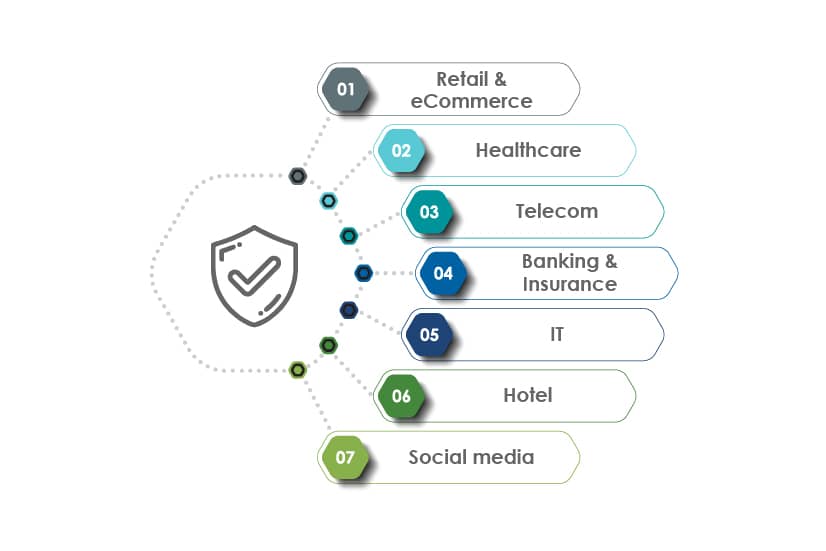
Retail & eCommerce:
According to Economic Times, a group of hackers attacked at least 570 e-commerce stores in 55 countries and leaked information of more than 184,000 stolen credit cards. They generated over $7 million from selling compromised payment cards.
Healthcare:
According to a recent Forbes report, cyber-attacks on US healthcare facilities in the year 2020 affected 17.3 million people, and resulted in 436 data breaches. Cyber-attackers can sell medical records on the dark web for up to $1,000 each.
Telecom:
According to Verizon Mobile Security Index 2021, 40% of respondents faced mobile device-related cyberattacks and 53% said the damage was significant. According to BusinessInsider, it is predicted that there will be more than 41 billion IoT devices by 2027 and the significant rise In cyber-attacks on IoT devices calls for the need for strict cybersecurity measures in the telecom sector.
Banking & Insurance:
According to CSI 2021 Banking Priorities Survey, 34% of the bankers reported that cybersecurity is their major concern. While 84% of the bankers view social engineering as the greatest cybersecurity threat in 2021. As per the responses collected, customer-targeted phishing and employee-targeted phishing are the major concerns prevailing in the banking sector.
IT Industry:
According to BBC News, Amazon said that its online cloud, fended off the largest DDoS attack in history. As per Amazon Web Services (AWS), the February 2020 attack had fired 2.3Tbps.
Hotel Industry:
Marriott in 2020 disclosed that a security breach impacted data of more than 5.2 billion hotel guests in one of its more impactful attacks in recent times
Social media:
According to BBC News, Twitter faced a major cyber-attack in which 130 accounts were targeted including the accounts of Barack Obama, Elon Musk, Kanye West, and Bill Gates. These accounts were used to tweet a Bitcoin scam to millions of followers by which attackers received hundreds of transfers, worth more than $100,000.
According to Business Insider recent report on April 04, 2021, nearly 533 million Facebook users phone numbers and personal data from 106 countries have been leaked online and security researchers warn that the data could be used by hackers to impersonate people and commit fraud.
Moreover, the Cybercrime magazine in its latest report states that cybercrime would cost the world $10.5 Trillion annually by 2025.
Various dominant types of cyber-attacks in recent times
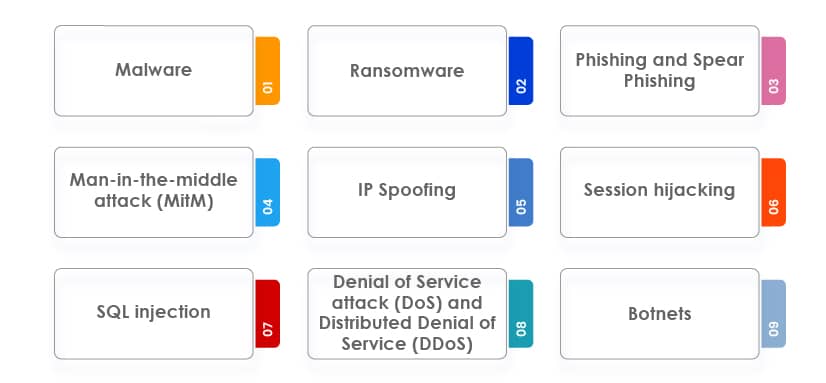
Malware:
It is malicious software that is installed by hackers on the victim’s system that damages the computer systems, servers, and networks. There are different types of malware such as worm, virus, Trojan, spyware, rootkit, adware, malvertising, ransomware, etc.
Ransomware:
It is the most common type of cybersecurity attack wherein the attacker encrypts the victim’s file and demands a huge amount of money or ransom to decrypt it. In this attack, the attacker threatens to publish sensitive or confidential data publicly on the dark web or blocks access to it until the ransom amount is paid.
Phishing and Spear Phishing:
It is a practice of sending malicious emails that appears to be from genuine sources. These emails also contain attachments that load malware onto the system of the user, by which attackers try to steal the personal information of the users.
Man-in-the-middle attack (MitM):
In this type of cyber-attack, a perpetrator intercepts the communication between the client and server with an aim to either eavesdrop or impersonate someone. The hackers try to steal personal information such as login credentials, account details, credit and debit card details, etc. Some of the main types of MitM attacks are IP spoofing, session hijacking, etc.
IP Spoofing:
The attacker tries to modify the IP address in the packet header to make the receiving computer system think it is from a legitimate or a trusted source. By this method, attackers gain access to computers and mine them for sensitive data. These infected computers are also used for malicious activities and for launching DDoS attacks further.
Session hijacking:
In this attack, the user session is taken over by an attacker. The attackers steal the victim’s session ID by either stealing the session cookie or by making the user click a malicious link containing a prepared session ID. After taking over the session, the attacker does malicious activities such as transfer money, steal the data, encrypt valuable data, and demand ransom to decrypt, etc.
SQL injection:
It is a code injection technique where the attacker injects malicious SQL code into the entry field for execution. This allows the attacker to view data that was not meant to be displayed or retrieved. It is a common issue with database-driven websites and websites that uses dynamic SQL.
Denial of Service attack (DoS) and Distributed Denial of Service (DDoS):
In this type, the attacker disrupts the organization’s servers or networks and floods them with fake or bot users to crash the normal functioning of the system. The most common types of DDoS attacks are TCP SYN flood, teardrop, smurf, ping of death, botnets, etc.
Botnets:
It is a collection of internet-connected devices which are infected by malware. Each infected device is known as a bot and is used to spread more bots. Using this technique, attackers steal credentials and data saved on devices and spread DDoS attacks.
These varied types of cyber-attacks continue to attack many businesses today and there is an exigency for ‘CYBER-SECURITY’ measures and especially ‘CYBER-SECURITY TESTING’ that should be leveraged by today’s businesses.
The emerging need for different types of security testing
The variety of cyber-attacks are growing tremendously and intruders have found new and smart ways of spreading malicious viruses and hacking systems to steal important and confidential enterprise and customer data. Cybercriminals have a variety of ways by which they can hack systems and gain unauthorized access to business-critical apps, networks, and servers. These rampant cyber-attacks can affect organizations in many ways such as loss of brand image and reputation, loss of customer trust, and can even result in legal and financial consequences.
There is a critical need for organizations to adopt robust security testing of apps, systems, networks, servers, and cloud infrastructure to prevent cyber-attacks. However, to ensure the safety of business-critical apps, businesses should know the below-mentioned security testing types.
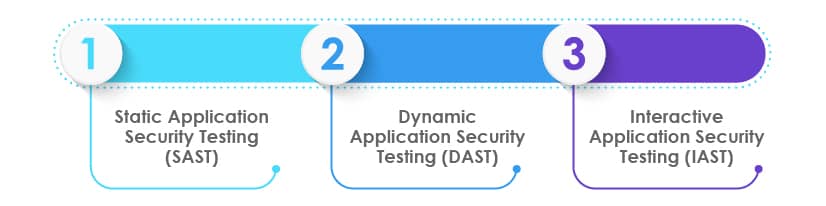
Static Application Security Testing (SAST):
It is a white box testing type where developers find security vulnerabilities in the source code of an application earlier in the software development life cycle. This testing method ensures that the app conforms to coding guidelines and standards.
Dynamic Application Security Testing (DAST):
Dynamic Application Security Testing is a black-box testing technique that allows testers to find security vulnerabilities and weaknesses in web apps. In this technique, the testers inject malicious data into the software just to mimic SQL injection and XSS attacks to identify common security vulnerabilities.
Interactive Application Security Testing (IAST):
It is a combination of both the SAST and DAST techniques. In this technique, an IAST agent is placed within an application that performs the analysis of the app in real-time. The IAST agent checks the runtime control and data flow information, configuration information, HTTP requests and responses, libraries, frameworks, and other components.
Other common types of security testing are:
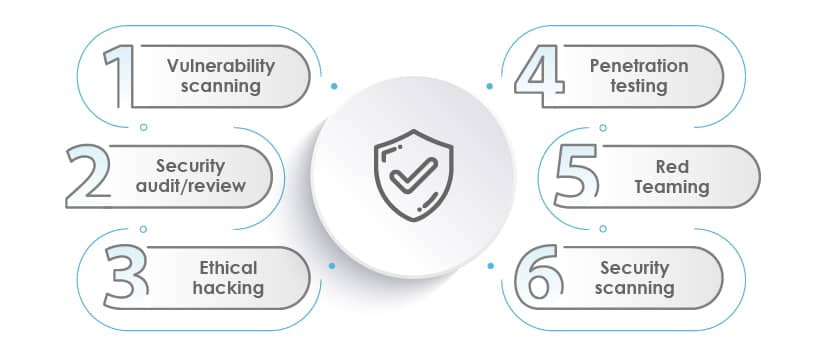
Vulnerability scanning:
In this testing technique, automated software is used to scan vulnerabilities in the system. It examines web apps to identify vulnerabilities like cross-site scripting, SQL injections, command injections, insecure server configuration, etc.
Security audit/review:
It is a cybersecurity practice that should be performed regularly. It helps organizations to assess the current security level of their system by detecting vulnerabilities and security loopholes. It can either be performed manually or can also be automated. Depending on the types of risks identified during the auditing, proper solutions are provided to the organizations.
Ethical hacking:
In this testing technique, a certified ethical hacker intrudes the organization’s system with legal and authorized permission to detect vulnerabilities in the system before a cyber-attacker finds and exploits it.
Penetration testing:
In this security testing method, the testers try to mimic the real cyber-attacks to find the vulnerabilities in the system. The two most common types of penetration testing are app penetration testing which revolves around finding technical defects in the software, and the other is infrastructure penetration testing in which testers examine the servers, firewalls, and other hardware.
Red Teaming:
It is a broader aspect of penetration testing where the internal or external team of security experts simulate real-time attacks on the organization. The security experts assess the environment without any prior knowledge. The specific evaluation is based on combining various security controls of the organization. The asset can be digital or physical based on the scope and the job of the security experts is to perform attacks, avoid detection, and provide sensitive data as proof.
Security scanning:
This security testing process involves identifying vulnerabilities in the app, software, system, networks. Both manual and automated security testing methods are used to perform this testing method. The insights obtained from these tests are duly used to provide solutions to fix issues.
Why today’s CXOs should leverage security testing?
Businesses across industry domains continue to face rampant cyber attacks and it has today cyber-security has essentially become a boardroom discussion. These cyber-threats have grown so large that their consequences significantly influence their valuation largely. Hence, network security and data privacy are today well know boardroom governance concerns. Hence, boards, directors, stakeholders and CXOs should have a greater vision and devote more attention to evaluate these risks and ensure to leverage security testing to safeguard from threats and vulnerabilities.
Today’s digital and connected world is more susceptible to the rampant cyber-attacks that continue to invade the businesses of their data and networks. Hence, to identify these vulnerabilities and safeguard systems and networks, different types of vulnerability assessments should be taken up. These assessments involve automatic scanning of the network infrastructure to have a complete overview of the system to known vulnerabilities, if any.
In addition, with the help of automatic scans, a series of checks are carried out on every system/application to understand their configuration in detail and detect any vulnerability. Moreover, penetration tests should also be carried out using different attack scenarios and combining manual techniques with automated tools to protect systems and data from any possible threats and vulnerabilities.
Therefore, today’s CXOs need to establish the appropriate cybersecurity measures in their respective organizations in the digital world to safeguard from any possible threats and vulnerabilities of their data, systems, networks, infrastructure, etc. CXOs should leverage security testing to get many benefits some of which have been given below.
Helps reveal real vulnerabilities:
It proactively helps businesses to identify, and fix vulnerabilities in their software, apps, networks, and servers. CXOs should take up security testing to ensure their organizations continue to deliver high-quality and secure services to their customers.
Ensures compliance to standards like PCI DSS, HIPPA:
There are certain legal standards that every organization is expected to follow. To ensure that the organization is complying with all the required standards, CXOs should leverage security testing. Failure in abiding by this legal standard can result in huge penalties to the organization.
Smoothens business continuity:
Every CXO wants their business to run seamlessly 24/7 which can be achieved with security testing. Regular security checks help businesses to eliminate situations of unexpected downtime or loss of accessibility which ultimately results in business continuity issues at times
Ensures security of IT systems, apps, networks & data:
As per a report by Hosting Tribunal, there is a hacker attack every 39 seconds. This clearly shows an alarming situation and CXOs need to protect their IT systems, business-critical apps, enterprise, and customer data from these rapidly increasing cyber-attacks and this is where security testing plays its role.
Helps to run a secure business during WFH:
Due to the current pandemic, employees continue to work from home and organizations require their employees to access the company’s data from a variety of devices, and through various networks including public WiFi and Hotspots. This has led to a rise in cybercrimes. As per a report published by The Hill’, US FBI reported that there has been a 400% rise in cybercrimes amid the COVID-19 pandemic. CXOs must ensure end-to-end security testing and should take strict cyber-security measures to normalize WHF and safeguard their businesses.
Ensures security of cloud solutions:
In the current era, cloud solutions have become a part of almost all organizations as they have started moving their IT systems to the cloud and therefore, cloud security has become the need of an hour. Though cloud architecture is much flexible than on-premise architecture as it allows running virtual machines and can store a huge amount of data. But still, the cloud continues to be more vulnerable to attacks. As per McAfee, there has been a 630% increase in external attacks on cloud-based services. Therefore, the security testing of cloud solutions is another aspect that CXOs should consider.
Keeps up brand image and reputation intact:
Even a single cyber-attack or data breach can negatively affect the image of an organization. According to Business Wire, 81% of consumers would stop engaging with a brand online after a data breach. This can adversely affect the brand image and revenue also. Therefore, every CXO should start investing in security testing methods to protect customer’s data and to preserve their brand image.
Increases security IQ of employees with policies in place:
Ensuring the security of data and systems is not the sole responsibility of IT teams. Rather it is the responsibility of every employee irrespective of their roles and this extends to CXOs as well. CXOs should align with subject matter experts to understand the requirements of security testing in their organization. CXOs can foster a culture of cyber-security in the organization by adopting stringent cyber-security policies
Ensures business with a proper cyber-defence plan
According to FireEye, 51% of the organizations do not have a proper cyber-defence plan. Hence, CXOs need to look at their organization’s cyber-defence capabilities and should take up end-to-end security testing along with formulating stringent security policies.
How we can help with your security testing assessments?
TestingXperts security testing teams have rich expertise in security testing and caters to diversified business needs. With a team of Certified Ethical Hackers (CEH), we help businesses to ensure that their application, networks, and servers are secure from all possible vulnerabilities and meets the stated security requirements like confidentiality, authorization, authentication, availability, and integrity. We primarily follow the OWASP (Open Web Security Project) guidelines in our security testing services along with PCI-DSS, HIPAA, SOX, WAHH, OSSTM, WASC, and NIST Standards as per the application-specific requirements.
Our Vulnerability Assessment and Penetration Testing (VAPT) / Comprehensive Security Testing Approach:
TestingXperts (Tx) enables a comprehensive vulnerability security testing approach that involves effective planning & execution along with collective risk assessment performed against multilayers of applications that includes the network, the hardware, and the software. This methodology helps to reduce re-work and ensures shorter time-to-market and cost-effectiveness. It also helps to save time and resources and protects brand reputation.
The actual process consists of security principles that have a specific set of test scenarios, which will be mapped to required regulatory compliances. Specifically, vulnerability testing involves deep investigation of the application to determine whether current patches are applied, whether it is configured in a manner that makes attacks more difficult, and whether the application exposes any information that an attacker could use to gain entry against other systems in the environment. Our security testing teams are well equipped with many latest security testing techniques.
Benefits of VAPT
– Vulnerability assessment helps to find security gaps if any in your web and mobile applications along with your networking infrastructure
– Validates the effectiveness of the existing security safeguards
– Helps to detect any security weaknesses even before cyber-attackers do
– Validates the effectiveness of security and system upgrades
– Helps to achieve and maintain compliance with all international and federal regulations
– Ensures to protect the integrity of assets in case of existing malicious code hidden in any of them
Talk to our security testing experts today — we’re here to help you safeguard your digital assets.
Discover more
Stay Updated
Subscribe for more info
