Recommended Blogs
Why Your Business Needs Data Security Posture Management?

- What is Data Security Posture Management (DSPM)?
- DSPM vs CSPM
- Core Components of DSPM
- What is the Role of AI in Data Security Posture Management?
- Top Benefits of Data Security Posture Management
- What are the Use Cases of Data Security Posture?
- What are the Top Tools for Data Security Posture Management?
- Why Do You Need Data Security Posture Management?
- How can Tx assist with DSPM?
- Summary
To do business in the modern world and remain competitive, businesses must shift from traditional network perimeters, initiate data democratisation, integrate AI/ML solutions, and adopt cloud-based technologies. And that’s a fact. On the other hand, these technological advancements have also introduced new security vulnerabilities.
The average data breach cost in 2024 is $4.88 million, a 10% increase from the previous year. The healthcare industry had the highest average data breach cost at nearly $9.77 million, while the financial sector was second at $6.08 million. To mitigate the security risks dwelling inside modern IT environments, companies need robust data security posture management (DSPM).
DSPM enables consistent management of data security threats and risks by continuously evaluating data security posture, identifying vulnerabilities, and implementing controls to reduce/mitigate those risks.
What is Data Security Posture Management (DSPM)?
Data Security Posture Management (DSPM) is a way to keep sensitive data safe in hybrid and multi-cloud systems by using AI and automation to find, sort, and protect it. It helps businesses uncover hazards more quickly, make sure they follow the rules, and address security holes before attackers can use them.
DSPM is a cybersecurity technology that helps businesses identify sensitive information across multi-cloud services or environments. It also assesses vulnerabilities, security threats, and regulatory non-compliance risks. Data security posture management offers insights and automation to assist security teams in addressing data compliance and security issues and preventing recurrence.
For example, organisations today handle and keep sensitive information, including PHI and PII, intellectual property, financial data, and more. This information is stored in many databases, cloud settings, and other places. DSPM helps keep this private information safe and speeds up the procedures of finding, detecting, classifying, protecting, and monitoring data.
As the amount of data and storage space grows, DSPM helps businesses find their sensitive data, regulate who may access it and how it can be used, and put data protection measures in place.
DSPM vs CSPM
| Data Security Posture Management | Cloud Security Posture Management |
| DSPM focuses on handling data security posture, including storage, access, and processing. | CSPM helps in securing cloud infrastructure by continuously monitoring and remediating cloud misconfigurations. |
| Ensures data security and compliance throughout its lifecycle. | Ensures compliance and security of cloud environments. |
| Protects sensitive data by identifying data access and storage vulnerabilities. | Focuses on securing cloud resources, including networks, services, and storage. |
| Covers data assets, databases, encryption, data privacy, and access controls. | Covers cloud infrastructure like virtual machines, networks, cloud services, and containers. |
| Assists in identifying risks associated with data exposure, leakage, wrong access, and compliance violations. | Assists in identifying risks such as cloud misconfigurations, network expires, and policy violations. |
| Key features include data discovery, encryption validation, classification, compliance checks, and access controls. | Key features include cloud resource scanning, compliance monitoring, configuration management, and automated remediation. |
| Monitors where sensitive data is stored, how it is used, and who has access to it. | Monitors cloud infrastructure configurations for security misconfigurations and vulnerabilities. |
| Ensure compliance with GDPR, CCPA, HIPAA, and other data protection regulations. | Ensure compliance with PCI DSS, NIST, SOC 2, CIS, and other cloud-specific compliance standards. |
| Automates data classification, policy enforcement, and encryption management. | Automates remediation of cloud misconfigurations and policy enforcement. |
| Identify and protect sensitive data in hybrid cloud environments. | Secure multi-cloud environments by detecting configuration drifts and vulnerabilities. |
Core Components of DSPM
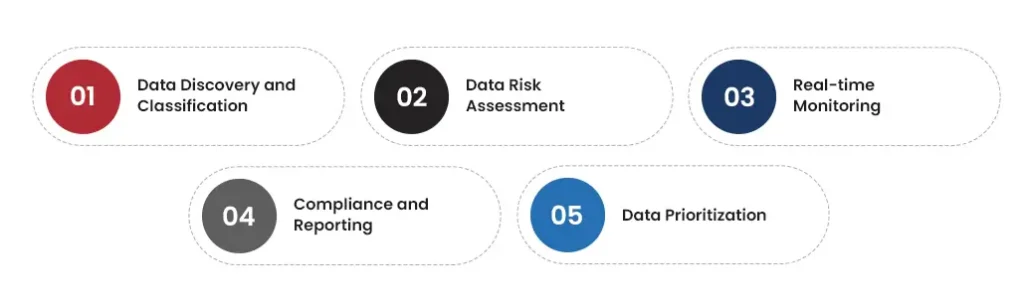
Data security posture management core components focus on ensuring data compliance, protection, and visibility across platforms. These components create an integrated and comprehensive process to secure sensitive data. Let’s take a look at some of the components of DSPM:
Data Discovery and Classification
Knowing where sensitive data lives is important. Data discovery creates an inventory that contains all sensitive data and helps identify where it’s stored. It also classifies all the data based on the regulatory frameworks governing it. Businesses can easily manage data access controls and decide what security protocols should be implemented to protect them.
Data Risk Assessment
Data security risk assessment starts with finding every environmental loophole. The process involves using automated tools to run regular checks against industry-specific data security standards and then creating tailored risk detection rules based on business requirements.
Real-time Monitoring
Ensuring critical business data protection is a continuous process that involves regularly scanning new data stores and identifying threats to data security. With real-time data monitoring, businesses can continuously supervise their data collection, storage, and usage. It would provide a holistic view of data and where, why, and how it is utilized.
Compliance and Reporting
Ensuring compliance with regulations and industry standards. It includes benchmarking, sending violation alerts, flagging security issues, and reporting compliance status.
Data Prioritization
This component prioritizes data based on its sensitivity level and the degree to which it is vulnerable to compromise. This allows businesses to identify potential attack paths and prioritize the data requiring urgent attention.
The Impact of AI on Data Security Posture Management
AI and ML are becoming more and more crucial to DSPM. They can automatically discover problematic access patterns and misconfigurations that human teams would not see. AI models look at huge volumes of data, mark sensitive information, and point up anything that isn’t right in real time, so you don’t have to do it yourself.
Here is how AI strengthens DSPM:
- Auto-detects misconfigurations: Finds risky setups and gaps in real time.
- Smart classification: Tags and organises sensitive data faster than manual methods.
- Predictive risk alerts: Spot unusual patterns and warn teams before small issues spread.
- Continuous learning: Improves detection over time as new threats appear.
Top Benefits of Data Security Posture Management
The primary benefit of integrating DSPM is that it accelerates the process of keeping data safe and secure, no matter where it is. Unlike other security postures focusing on cloud, applications, devices, networks, identity, etc., DSPM’s main focus is data only. Let’s take a quick look at some of the benefits of implementing data security posture management:
- DSPM helps avoid legal actions and fines by auditing business policies against data protection rules and regulations, ensuring improved data security for partners and customers.
- Seamlessly connect with DevSecOps workflows for early risk mitigation whenever they appear in the app development lifecycle.
- Pinpoint abandoned data stores as they are easy targets for cyberattacks due to a lack of supervision, and businesses can easily transfer them to affordable repositories for cost savings.
- It helps create data policies and controls (even across multi-cloud and SaaS environments) according to organisational needs and data sets.
- It enables automation to continuously monitor and optimise security posture while enabling teams to address high-priority data vulnerable to security breaches.
- DSPM helps secure all types of data, including data located in SaaS, PaaS, multi or public cloud, and hybrid or on-premises infrastructure.
What are the Use Cases of Data Security Posture?
Each industry has its own way of handling sensitive information and its own set of threats. DSPM changes to match these facts and maintains organisations safe and compliant. Find out how it works in other fields:
- Healthcare
Healthcare providers handle huge amounts of protected health information (PHI) and Electronic Health Records (EHRs). DSPM helps discover where this data lives, control who can access it, enforce HIPAA requirements, and spot suspicious behavior fast and cut the risk of costly breaches.
- Finance
Banks, insurance firms, and fintech process customer PII, transactions, and confidential financial data every second. DSPM safeguards this critical information, checks for regulatory gaps under GLBA and PCI DSS, and makes sure only the right people can access high-value data assets.
- Retail
Retailers store payment card details and shopper profiles across online stores, POS systems, and cloud apps. DSPM locks down customer data, ensures PCI DSS compliance, spots abandoned or risky data stores, and helps prevent breaches that can hit brand trust hard.
- Government
Government agencies deal with citizen records, legal files, and classified information. DSPM provides full visibility, tight access controls, and helps meet strict public sector compliance rules.
- eCommerce
Online businesses collect payment details, order histories, and customer profiles across multiple platforms. DSPM locates and locks down this data, reduces fraud risks, and keeps privacy compliance on track.
- Manufacturing
Manufacturers keep track of IP, design documentation, and supply chain data that is spread out among facilities and partners. DSPM shows where sensitive files are kept, controls who can see them, and keeps trade secrets safe against theft or leakage.
What are the Top Tools for Data Security Posture Management?
Choosing the right DSPM tool can make all the difference. The best tools blend AI, automation, and deep visibility to help security teams stay ahead of risks. Here are a few tools for data security posture management:
- Varonis: It is well-known for data security and governance and helps discover, classify, and protect sensitive data across platforms.
- BigID: Offers a full data security and privacy platform with strong discovery, classification, and risk management features.
- Palo Alto Networks Prisma Cloud DSPM: It integrates with other security tools to provide data classification, risk assessment, and policy enforcement.
- Securiti Data Command Centre DSPM: This tool supports breach and compliance management, real-time data streaming, and easy integration with other security systems.
- Sentra: Cloud-native focus, securing data across cloud services, containers, and virtual machines.
- Forcepoint DSPM + DDR: It combines data discovery, classification, and remediation with adaptive risk protection.
- Cyera: Uses AI and ML to discover and classify data, shining light on your real data attack surface.
- Strac: Provides DSPM capabilities with handy integrations for platforms like Zendesk, Slack, and Gmail.
Why Do You Need Data Security Posture Management?
Security tools and technologies protect sensitive data by restricting unauthorised network access or by identifying and blocking malicious behaviours by users, APIs, IoT devices, etc. Although these technologies have upscaled data security and threat detection and remediation capabilities, the rapid adoption of cloud-native technologies, AI, and ML has increased concerns regarding data security risks. These technologies don’t always address security vulnerabilities, leaving sensitive business data at risk of breaches and compliance violations.
One of the significant risks is ‘Shadow Data,’ which means data copied, replicated, or backed up to a location that’s not governed or managed by the same policies, security teams, or controls that operate the original data. The major contribution to shadow data is AI or ML modeling, which requires a lot of data. To train AI/ML models, businesses usually expand data access to more users, some of whom don’t even have the basic knowledge of data security and governance. And the adoption of a hybrid or multi-cloud environment spreads this risk further.
How can Tx assist with Data Security Posture Management?
Tx can assist with Data Security Posture Management (DSPM) by providing a comprehensive approach to protect and manage your data security across various environments, including cloud, hybrid, and on-premises systems. Here’s how Tx can help:
- We identify vulnerabilities, misconfigurations, and potential risks in your data environment, offering actionable insights for mitigation.
- Tx uses AI-driven tools to monitor and detect abnormal data activity, ensuring proactive threat detection and compliance.
- We implement robust encryption, access controls, and policies to safeguard sensitive data at every stage.
- Tx ensures adherence to regulatory standards such as GDPR, HIPAA, and PCI-DSS by auditing data security practices and aligning them with industry best practices.
- Our team is prepared to respond to data security incidents swiftly, minimizing potential damage and ensuring business continuity.
Our in-house accelerator, Tx-Secure, is a powerful security operations platform for SIEM, compliance monitoring, threat intelligence, and more. The tool offers advanced security analytics, threat detection capabilities, and comprehensive monitoring, analysis, and response for security-related data across your business infrastructure. Its key capabilities include the following:
- Real-time threat detection
- Vulnerability management
- File integrity monitoring
- Malware detection
- Compliance monitoring
- Network intrusion detection
- Log management and analysis
- Comprehensive visibility
Summary
Data security posture management (DSPM) is an integral part of modern business operations and data security strategy. Data’s growing demand and value raise concerns about the consequences of data mishandling, which is why businesses should prioritize DSPM. By leveraging DSPM, businesses can secure sensitive data, improve brand value, and maintain customer trust. Tx, the leading security testing services provider, can assist in establishing a strong data security platform. It will help you automate data discovery, risk remediation, prioritization, and monitoring processes.
Ready to secure your data with DSPM? Contact Tx today to learn how we can help protect your business from cyber threats.
FAQs
Data Security posture management is a security approach which focused on continuously assessing, monitoring, and managing an organization’s data risks. It provides visibility into data assets, identifies vulnerabilities, and ensures compliance by enforcing policies across cloud and on-premises environments.
Cloud environments are dynamic, which is making data exposure risks higher. Data security posture management helps organisations maintain control over data security, detect misconfigurations, prevent data leaks, and ensure compliance in real-time within cloud infrastructures.
Key features include automated data discovery, risk assessment, continuous monitoring, policy enforcement, compliance reporting, anomaly detection, and integration with cloud platforms and security tools, providing real-time visibility and control over sensitive data.
Industries handling sensitive or regulated data, such as finance, healthcare, retail, government, and technology, benefit the most from DSPM to protect customer information, ensure regulatory compliance, and reduce the risk of costly data breaches.
Top DSPM tools include Varonis, BigID, Symmetry Systems, Cyera, and Spirion. These platforms provide advanced real-time data discovery, risk analytics, compliance monitoring, and automated remediation capabilities tailored for cloud and hybrid environments.
Discover more
