Recommended Blogs
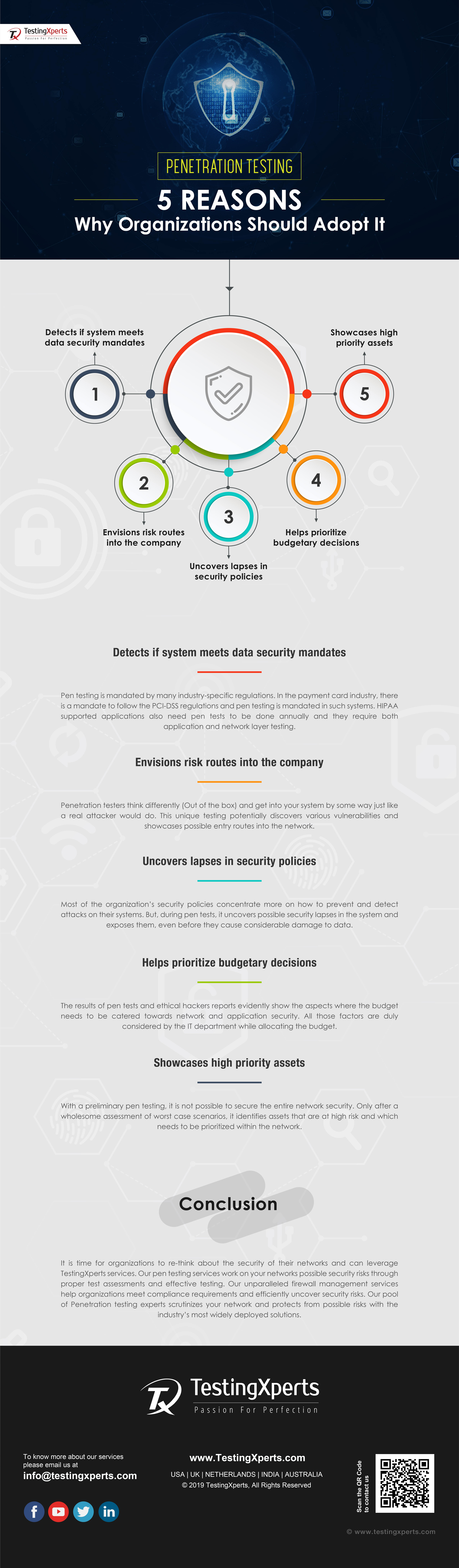
Penetration Testing – 5 Reasons Why Organizations Should Adopt It

In today’s cyber world, with vulnerabilities all around, security is a vital component for every organization. If there are lapses in the infrastructure and network security, companies face unexpected costs and will not be able to run their businesses successfully. With ever-increasing vulnerabilities and cyber attacks, companies should protect their applications and digital assets from cyber threats; web applications are more susceptible to these attacks. Penetration testing is one type of security testing that should be taken up to detect recently discovered or any previously known vulnerabilities or weaknesses in their network, computer systems and applications. This type of testing aims to identify vulnerabilities in a system that might impact the integrity and confidentiality of data by emulating a real attack.
When Should Pen Testing be taken up?
Pen testing should be taken up after deployment of new infrastructure and applications, or when changes are made to firewalls, firmware updations, or when any upgrades and patches are taken up for systems. This testing effectively checks the organization’s ability to detect intrusions and breaches, if any. There are many reasons why organizations should focus on penetration testing.
Discover more
Stay Updated
Subscribe for more info