
- The Current State of Cybersecurity Threats and Vulnerabilities
- An Overview of Vulnerability Assessment
- 3Major Impacts of Cybersecurity Breaches on Digital Businesses
- Types of Vulnerability Assessment Tools for Digital Businesses
- Key Takeaways of Effective Security Testing
- Conclusion
- How TestingXperts Helps Businesses with Vulnerability Assessments?
The Current State of Cybersecurity Threats and Vulnerabilities

Digital businesses across industries continue to deal with rampant cyber-attacks. Hence, different vulnerability assessments should be taken to identify these vulnerabilities and safeguard systems and networks. These assessments automatically scan the network infrastructure to have a complete system overview to know any vulnerabilities and perform efficient security testing thereafter.
An Overview of Vulnerability Assessment

A comprehensive vulnerability assessment enables digital businesses to identify, segregate, and prioritize vulnerabilities that may occur in a network infrastructure, computer systems, and software. Generally, a vulnerability is identified as a security loophole that hackers may exploit to expose the organization to cyber threats or risks. The process of vulnerability assessments includes leveraging automated testing tools, like security scanners, that analyze the network or application and share the vulnerability results in an assessment report.
Major Impacts of Cybersecurity Breaches on Digital Businesses
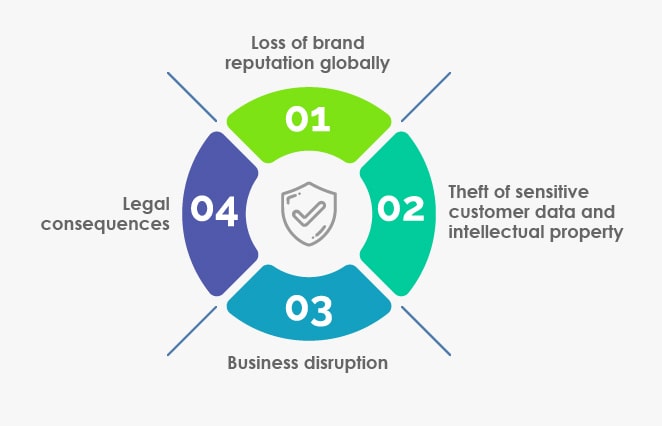
Loss of brand reputation globally
Cyber-attacks have caused businesses to lose their customer’s and stakeholders’ trust, especially if the company has failed to protect their sensitive data. Invariably, such a reputation loss fails to attract the best talent, suppliers, or even investors, leading to business disruption.
Theft of sensitive customer data and intellectual property
Continuous attacks by cybercriminals have led to monetary and data losses. The stolen data is further sold on the dark web, where hackers demand hefty ransoms. In the case of intellectual property theft, it may lead to the loss of years’ worth of effort and investment.
Business disruption
Cybercrimes cause small businesses more damage when compared to large businesses or large corporations. According to a report, 43% of cyber-attacks are aimed at small businesses, but only 14% are prepared to defend themselves. Due to specific cyber-attacks, many leading corporate websites have gone down, suffering many hours of business disruption in recent times.
Legal consequences
Businesses must protect the sensitive data of customers and employees. If this data is compromised, it showcases that the organization has not followed appropriate security measures and may be levied with regulatory sanctions and legal consequences.
Types of Vulnerability Assessment Tools for Digital Businesses
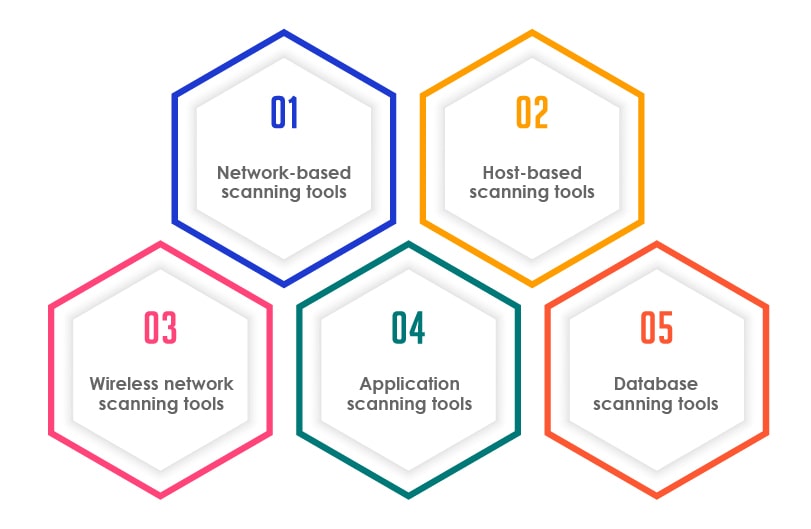
Network-based scanning tools
These tools identify potential network security attacks and detect vulnerable systems on both wired as well as wireless networks.
Host-based scanning tools
These vulnerability assessment tools are used by testers to identify the potential vulnerabilities on servers or other network hosts used by digital businesses. Host-based scanning tools scan the application for open ports and services, and share key insights on the configuration settings and patch history of scanned systems.
Wireless network scanning tools
These tools are leveraged to scan the Wi-Fi network of a digital business and identify the security weaknesses. These tools scan and identify the potential access points and ensure that the wireless networks of digital businesses are configured securely.
Application scanning tools
These vulnerability assessment tools are used to test websites and mobile applications for the possible software vulnerabilities and misconfigurations.
Database scanning tools
Testers use these tools to identify the vulnerabilities that may be a reason to cause database-specific attacks. The attacks may be in the form of SQL and NoSQL injection, and other general vulnerabilities and misconfigurations in a server.
Vulnerability Assessment vs Penetration Testing
| Vulnerability Assessment | Penetration Testing | |
| Purpose | The primary purpose of a vulnerability assessment is to identify and categorize vulnerabilities in your system. It aims to create an inventory of potential weaknesses that attackers could exploit.
|
Penetration tests, on the other hand, go beyond identifying vulnerabilities. Their primary purpose is to simulate real-world attacks and assess the effectiveness of your overall security measures. |
| Approach | This process involves using automated tools to scan your system for known vulnerabilities. The emphasis is on identifying as many vulnerabilities as possible within a given scope. | Penetration tests simulate actual attacks by attempting to exploit vulnerabilities to gain unauthorized access. They focus on understanding how an attacker can penetrate your firewalls. |
| Depth of Analysis | These assessments provide a broad view of potential vulnerabilities but might not delve deeply into how these vulnerabilities can be exploited or the potential impact of an attack.
|
Penetration test involve a more comprehensive analysis. They explore how different vulnerabilities can be combined and leveraged to escalate an attack and potentially compromise sensitive data or systems. |
| Real-World Simulation | While vulnerability assessments identify weaknesses, they don’t simulate real-world attacks or consider the tactics attackers might use.
|
Penetration tests replicate the actions of malicious hackers, offering a realistic simulation of how an attacker might target your systems. It helps organizations understand their actual vulnerabilities and potential risks. |
| Reporting | Vulnerability assessments typically generate reports listing identified vulnerabilities, their severity, and potential impact. These reports serve as a guide for prioritizing fixes. | Penetration test reports provide a detailed account of the different stages of an attack, from initial exploitation to potential data exfiltration. This information is valuable for understanding the complete attack lifecycle. |
| Frequency | Assessments are often conducted regularly to keep up with the evolving threat landscape. They help organizations track improvements and detect new vulnerabilities. | Penetration tests are usually conducted less frequently and are often scheduled after significant system updates or changes. They provide a comprehensive view of an organization’s security posture. |
Key Takeaways of Effective Security Testing
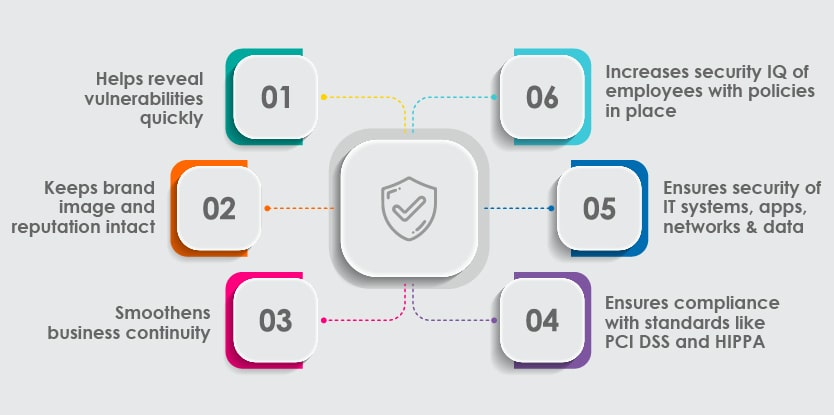
Helps reveal vulnerabilities quickly
It proactively helps businesses to identify and fix vulnerabilities in their software, apps, networks, and servers. Digital businesses should take up security testing to ensure their organizations continue to deliver high-quality and secure services to their customers.
Keeps brand image and reputation intact
Even a single cyber-attack or data breach can negatively affect the image of an organization.
According to Business Wire, 81% of consumers would stop engaging with a brand online after a data breach. This can adversely affect the brand image and revenue also. Therefore, digital businesses should invest in end-to-end security testing services to protect customer data and preserve their brand image.
Smoothens business continuity
Every business strives to operate seamlessly 24/7, which is achieved with practical and robust security testing methods. Regular security checks help businesses to eliminate situations of unexpected downtime or loss of accessibility, which could result in business continuity issues at times.
Ensures compliance with standards like PCI DSS and HIPPA
There are specific legal standards in every industry that corresponding organizations are expected to follow. Failure to do so may lead to legal obligations and fines. To ensure compliance with all the required standards, businesses should leverage security testing to avoid any penalties due to noncompliance.
Ensures security of IT systems, apps, networks & data:
As per Cybersecurity Ventures, a new cyber-attack hits every 11 seconds. This clearly shows an alarming situation; businesses must protect their IT systems, business-critical apps, and enterprise and customer data from these rapidly increasing cyber-attacks. This is where security testing plays its role.
Increases security IQ of employees with policies in place
Ensuring the security of data and systems is not the sole responsibility of IT teams. Vulnerability assessments help to understand the security testing requirements in the organization and foster a culture of cyber-security in the organization by adopting stringent cyber-security policies.
Conclusion
Cyberattacks have been on the rampage and pose a significant risk to business apps, data, systems, networks, and the risk of losing customer trust and the organization’s reputation. Today’s businesses should ensure robust cyber security readiness by leveraging end-to-end security testing.
Businesses should outsource security testing to the best outsourcing partner to protect their businesses from cyberattacks and ensure vulnerability-free. Outsourcing cyber security testing can help enterprises to achieve faster incident response time, save high costs, and overcome cyber threats and vulnerabilities.
How TestingXperts Helps Businesses with Vulnerability Assessments?

TestingXperts security testing teams have rich expertise in security testing and cater to diversified business needs. With a team of Certified Ethical Hackers (CEH), we help businesses to ensure that their application, networks, and servers are secure from all possible vulnerabilities and meets the stated security requirements like confidentiality, authorization, authentication, availability, and integrity.
Advanced DevOps Security Accelerator for Digital Businesses – Tx-DevSecOps
For digital businesses to reap more benefits concerning code security, TestingXperts Test Center of Excellence (TCoE) has developed an in-house accelerator, Tx-DevSecOps. This first-of-its-kind dynamic DevOps security accelerator offers a framework for continuous security testing and vulnerability management.
With Tx-DevSecOps accelerator, today’s digital businesses should leverage this high-speed and shift-left approach to continuous security testing. Its framework seamlessly embeds security checks within your existing DevOps environment to track and remove modern threats and helps to deliver secure software.
With the Tx-DevSecOps accelerator in place, it becomes easier to compile bug reports from different tools to a single dashboard, identify false positives, and track vulnerabilities efficiently. The application security can be checked at every stage of DevOps development and deployment. Typically, every stage produces some security output vulnerability issues, which are made visible in the vulnerability management dashboard.
Tx-DevSecOps accelerator helps with relevant security checks at each of the below stages:
• Pre-Commit Hooks
• IDE Security Plugin
• Secrets Management
• Software Composition Analysis (SCA)
• Static Analysis Security Testing (SAST)
• Dynamic Analysis Security Testing (DAST)
• Security in Infrastructure as Code
• Compliance as Code (CAC)
• Vulnerability Management
• Alerting and Monitoring
• Asset Monitoring
Tx-DevSecOps Issue Tracker
• Vulnerability management platform integrated with SAST and DAST tools manages:
• Clients and projects
• Access control
• Vulnerability life cycle
• Common Vulnerability Scoring System (CVSS) over the past 5 releases
• Removal of duplicate vulnerabilities from the report
• Access to interactive reports
• Details of all open vulnerabilities along with their severity and other technical details
• Automated notifications of identified vulnerabilities across major collaboration tools (Slack, Jira, MS Teams, etc.)
• This section should talk about benefits of Vulnerability Assessment. Currently it is about benefits of Security Testing which is a broader term.
Discover more
Get in Touch
Stay Updated
Subscribe for more info




