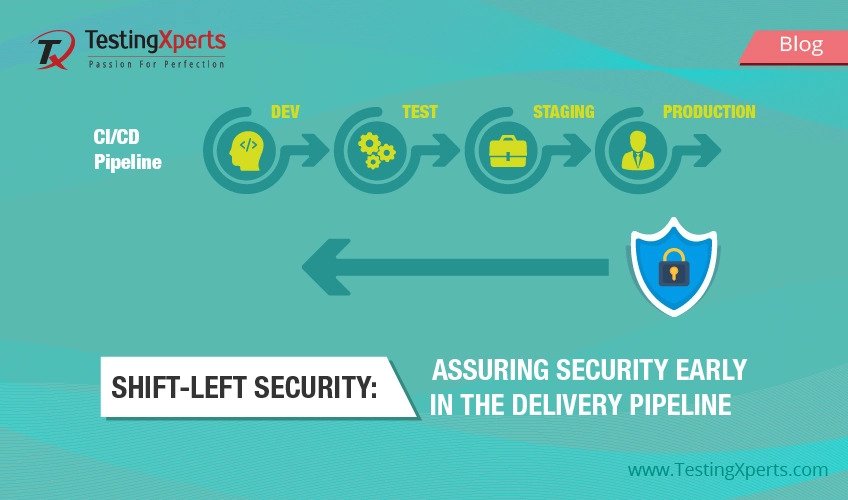
Developers and testers often face constant pressure to release new features and fix bugs quickly to deliver software quickly. To achieve faster releases, teams adopt a DevOps Continuous Integration (CI)/Continuous Delivery (CD) pipeline that helps quickly build, test, and add incremental updates faster. However, it has been observed that the security aspect of the software is sometimes compromised due to the rising need for speed of delivery. Post-production vulnerability issues discovered in the software pose a significant risk to the data and systems. These security loopholes ultimately delay the software delivery process, which affects the brand and customer loyalty, leading to the loss of time and costs. Thus, DevOps teams need to embed security testing into the DevOps CI/CD pipeline to reduce the chances of security issues going into production.
Content
- An overview of DevOps CI/CD pipeline
- Different stages of the DevOps CI/CD pipeline
- How is security testing embedded at each stage of the DevOps CI/CD pipeline?
- Significance of embedding security testing into DevOps CI/CD pipeline
- Major security testing types businesses should leverage
- Conclusion
- How can TestingXperts (Tx) help?
An overview of DevOps CI/CD pipeline
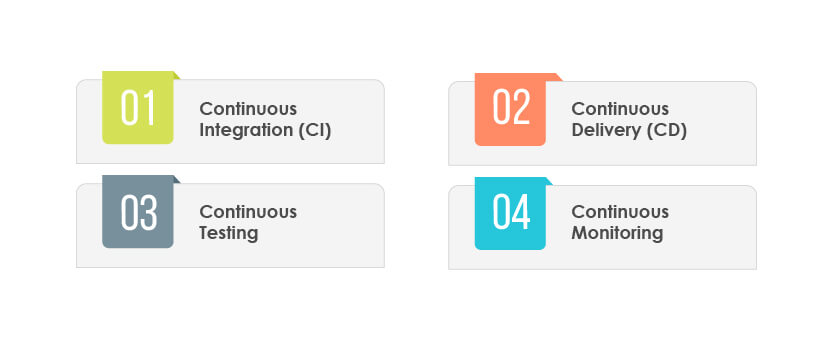
DevOps is an evolution from agile methodology and is a software development approach that brings software development and operations teams together. Its main aim is to break the traditional silos between cross-functional teams. This methodology promotes collaboration between teams and ensures faster, and quality releases are delivered to the customer. DevOps CI/CD pipeline stages include:
Continuous Integration (CI):
In this stage, the developer frequently commits changes to the source code. The new code that supports the latest functionalities is continuously integrated with the source code.
Continuous Delivery (CD):
It is an extension of CI, where the software delivery process is automated to ensure reliable and easy deployment into production at any time.
Continuous Testing:
In this phase, the developed software is continuously tested for bugs leveraging automation testing tools such as TestNG, Selenium, JUnit, UiPath Test Suite, etc.
Continuous Monitoring:
In this phase, the software is continuously monitored to ensure its seamless functioning, leveraging continuous monitoring tools such as Nagios, Splunk, Sensio, etc.
Different stages of the DevOps CI/CD pipeline
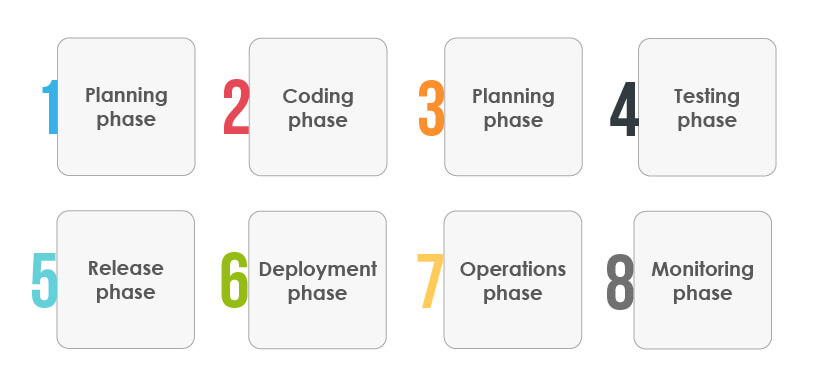
Planning phase:
In this stage, requirements and feedback are gathered from the stakeholders and customers to build a product roadmap for product development. This step also involves deciding on the best practices and policies that should be followed for a successful DevOps process.
Coding phase:
Developers are involved in this stage and are responsible for writing the code and building the product. In this phase, tasks are divided among the developers, and they write the code according to their tasks.
Build phase:
Developers commit their code to the shared code repository at this stage. Integration issues are resolved by continuously checking the code changes, and this stage also includes running builds and tests.
Testing phase:
Once the build succeeds, the software is thoroughly tested. If any new feature or functionality is added, the software is again tested using the regression testing method to ensure its proper functioning.
Release phase:
The build is ready for deployment to the production environment at this stage. Depending on the DevOps maturity, an organization can choose an automated deployment technique.
Deployment phase:
The build is released into the production environment in this deployment phase, and various tools are leveraged to automate the deployment process.
Operations phase:
In this stage, operations teams ensure the build is running smoothly. Also, customer feedback is taken up to shape the product’s future development.
Monitoring phase:
It is the final stage of DevOps, where the DevOps pipeline is monitored. Monitoring is done to ensure the software build works well in the production environment and there are no bottlenecks that affect the software functioning or performance.
DevOps CI/CD pipeline helps teams release software faster, but the security aspect of the software should be monitored closely. Therefore, it is essential to embed security testing at each stage of DevOps CI/CD to ensure quality and secure releases.
How is security testing embedded at each stage of the DevOps CI/CD pipeline?
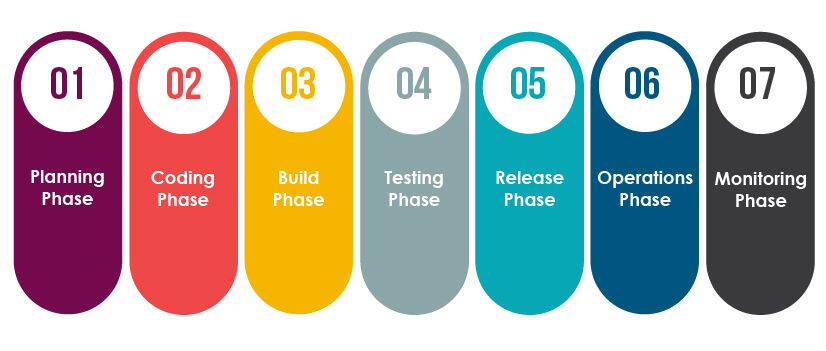
Planning phase:
• The planning stage involves threat modeling and preparation of security policies
• DevSecOps teams identify the security requirements, potential security threats, and vulnerabilities, quantify threats and prioritize remediation methods
• It also involves the preparation of security policies to improve the cyber-security readiness of an organization
Coding phase:
• This stage involves coding of the software, and in-depth code reviews are conducted to ensure the correctness of the code
• Best practices and guidelines of software development are followed to ensure the robustness of the software build
Build phase:
• This stage involves source code management in which Static Analysis of the source code or Static Application Security Testing (SAST) and dependency scanning are performed
• The main aim of integrating these tests into the CI/CD pipeline is to ensure there are no security issues while the software components are being developed and integrated
• During this stage, isolated changes are immediately tested, reported, and then added to a central repository
Testing phase:
• During this stage, the application is deployed to test servers or QA environment
• At this stage, dynamic scanning or Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and Penetration tests are conducted.
• During this stage, the DevSecOps teams create automated security testing attacks for penetration testing or API testing to ensure application and the infrastructure are free from vulnerabilities
• Continuous testing of the software at this stage ensures identification and removal of all new or missed vulnerabilities
Release phase:
• During this stage, the completely developed and tested application is deployed to servers
• At this stage, compliance, and validation of software are checked against all necessary guidelines, best practices, policies, and protocols.
• It ensures software does not violate any security policies and ensures continuous testing to remove all possible software bugs
Operations phase:
• At this stage, security testing is integrated by implementing Infrastructure as Code (IaC) and Secret management processes
• IaC ensures managing and provisioning of infrastructure through code instead of doing it manually, which ultimately eliminates the chances of human-prone errors and ensures the security
Monitoring phase:
• This is the last stage in which failure or automatic error recovery process is set up to ensure if failures are overcome such that productivity does not go down
• It also involves the use of logging and alerting methods, threat intelligence methods, and vulnerability disclosure methods to ensure robust security
• If any error is discovered at this stage, it should be treated as a normal run-down failure and must be rolled back to the previous versions to ensure users are not impacted
Significance of embedding security testing into DevOps CI/CD pipeline
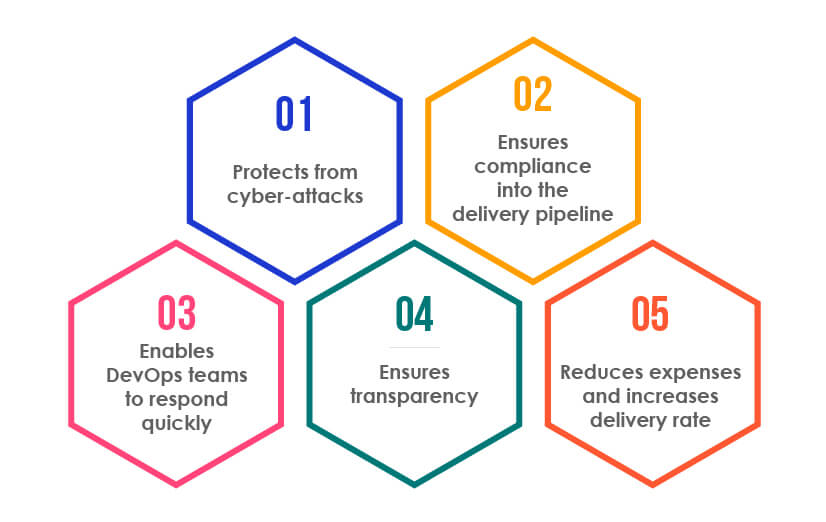
Protects from cyber-attacks:
Security testing at each stage of the DevOps CI/CD pipeline ensures the removal of security loopholes or vulnerabilities from software that could otherwise be exploited by cyber attackers if left unidentified.
Ensures compliance into the delivery pipeline:
Security testing involves checking bugs, compliance, policies, and best practices to ensure successful DevOps implementation.
Enables DevOps teams to respond quickly:
Security testing at each stage of the DevOps lifecycle gives teams the ability to respond to changes quickly.
Ensures transparency:
Security testing in DevOps ensures openness and transparency as software issues are shared across teams with close stakeholders collaboration.
Reduces expenses and increases delivery rate:
Integrating security testing into the delivery pipeline helps identify and remove security defects, which ultimately reduces overall expenses. It also improves the delivery rate as robust software verification ensures faster bug fixes and rapid delivery.
Major security testing types businesses should leverage
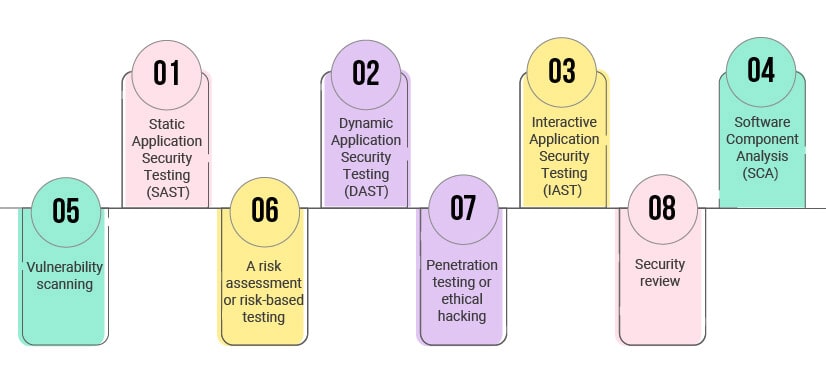
Static Application Security Testing (SAST):
It is a white box software testing technique that involves the process of examining source code for security defects. In this process, security issues or vulnerabilities are identified and mitigated early in the DevSecOps process.
Dynamic Application Security Testing (DAST):
It is a black box software testing method that involves testing the application as it is running to find vulnerabilities that a cyber-attacker could exploit.
Interactive Application Security Testing (IAST):
IAST is a software testing method in which software instruments are used to assess an application in real-time. In IAST, agents and sensors are run to continuously analyze the application performance during automated, manual, or both situations. Further, this security testing method seamlessly integrates into the DevOps CI/CD pipelines.
Software Component Analysis (SCA):
It is the process of automating the visibility into Open-Source Software (OSS) use for risk management, security, and licenses compliance. It involves integrating OS security and license scans in the DevOps environment to scan code and identify dependencies in the built environment.
Vulnerability scanning:
It is the process of identifying and rectifying weaknesses or flaws present in the software. Some of the common software vulnerabilities that can be rectified with this testing type include missing data encryption, authentication for critical functions, buffer overflows, insecure interactions between the software components, etc.
A risk assessment or risk-based testing:
Risk assessment is the process of identifying and prioritizing probable risks associated with the software. The DevSecOps teams prioritize the tests of features and functions in software based on certain factors such as the risk of failure, the function importance, or the impact of failure.
Penetration testing or ethical hacking:
A professional and authorized ethical hacker tries to simulate cyberattacks in this software testing technique. The main purpose of this test is to identify the security loopholes present in the system, which can otherwise be exploited by cyber-attackers if left unidentified or unresolved.
Security review:
It is the process of safeguarding the entire DevOps environment by ensuring stringent security policies, strategies, best practices, processes, and technology.
Conclusion
Today’s businesses are rapidly adopting DevOps to deliver faster and quality software to their customers. However, due to the constant pressure to deliver software quickly to customers, QA teams often push security testing to later stages. This delay in the security testing process ultimately delays the delivery process more, as some security issues might be identified at later stages. In order to overcome this challenge, businesses should adopt security testing in the DevOps process.
In DevOps, where every stage or process is continuous, QA teams should ensure continuous security testing by embedding security testing procedures at each stage of the CI/CD pipeline. Security testing in DevOps ensures early identification and removal of security issues at each stage of the DevOps delivery pipeline, and it also speeds up the software delivery process. Thus, integration of security testing is important for businesses and requires an expert DevOps implementation partner such as TestingXperts.
How can TestingXperts (Tx) help?
TestingXperts (Tx), a next-gen QA and software testing services provider, has been at the forefront of enabling security testing services for businesses across industries. With the help of our highly skilled team of security testers and in-house accelerators, we have served several industry-leading clients. Our security testing teams follow a customer-centric approach and evaluate business needs in close collaboration with the client and other stakeholders to deliver secure solutions. Tx has developed an in-house framework: Tx-PEARS that can be leveraged to fulfill all the non-functional testing requirements, including the continuous monitoring of infrastructure in production and lower environments. Speak to our teams for more information on Tx-PEARS
Discover more
Get in Touch
Stay Updated
Subscribe for more info