
In a single year, several cyber security trends emerged:
- 66% of organizations effected with Ransomware in 2023
- 44.7% of data breaches with the abuse of credentials
- 400% increase in the IoT malware attacks across various industries, manufacturing being the most targeted one.
Organizations are struggling with security breaches, and cybersecurity monitoring can be a game changer, by enabling learning about the security threats in real time and respond faster than cyber attackers can move.
Despite making notable investments in security technologies, organizations continue to struggle with security breaches. Their problems are quick to evolve tactics and stay ahead of the technology curve. The challenge is these few events can wear down the trust of customers, regulators, and investors more than a data breach of the digital operations.
People are already challenged to effectively analyze the data flowing into the Security Operations Center (SOC) across the security tech stack. This does not include the information feeds from application data, network devices, and other inputs across the wider technology stack that are the key targets of the advanced attackers looking for using new malware.
What is Cybersecurity Monitoring?

Cybersecurity monitoring includes the real-time or near real-time observation of events and activities across the network. It permits the organizations to ensure that security measures safeguard the integrity, availability and confidentiality of data assets that remain uncompromised. In addition to this, it helps in checking and addressing threats or vulnerabilities before they escalate into a data security incident.
The important thing to understand is, whether real-time or near-real-time, cyber threat monitoring is a dynamic process. Organizations must manage this process actively to keep pace with the quickly evolving cyber risk landscape, and ongoing changes within their own operational and enterprise architecture environment.
The US federal agency also highlights that continuous monitoring is an important element of enterprise risk management frameworks. It supports the implementation of a rigorous information security continuous monitoring (ISCM) strategy. This strategy aims to maintain an ongoing awareness of vulnerabilities, security, and threats to support organizational risk management decisions.
How does Cybersecurity Threat Monitoring Work? Let’s break it down:
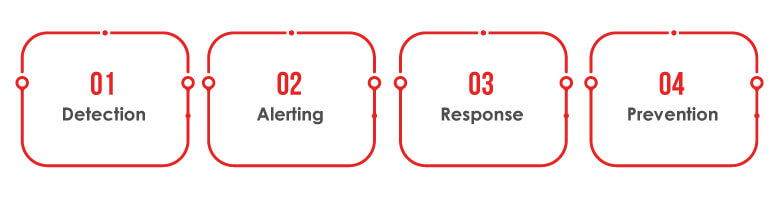
Cybersecurity threat monitoring works by regularly analyzing system activities, traffic, and data logs to perceive and respond to potential security threats in real-time. It includes the use of multiple tools and technologies, like Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), and behavioral analytics, to recognize abnormal patterns or activities indicating a cyber threat.
For Example: Monitoring for Phishing Attacks
There’s a company that implements cybersecurity threat monitoring to safeguard the email system from phishing attacks. The system scans incoming emails for suspicious characteristics, like unusual sender addresses, misleading URLs, or attachments with the harmful code.
Detection: The monitoring system recognizes an email from an unknown sender with a link that appears to be a trusted website but has a slight misspelling (e.g. paypal.com vs. Paypall.com). It flags such an email as a phishing attempt.
Alerting: When detected, the system immediately generated an alert and notifies the security team. This alert involves details like sender’s address, the email’s content, and the suspicious link.
Response: On receiving the alert, the security team quickly analyzes the email and confirms it as a phishing attempt. They block the sender and take action and notify the employees to be cautious of similar emails.
Prevention: To prevent future incidents, the system is updated to automatically block similar emails, and employees receive training on recognizing and reporting phishing attempts.
This way, cybersecurity threat monitoring enables the organization to detect, respond to, and prevent phishing attacks, while protecting sensitive information and maintaining the integrity of its network.
AI defense against today’s cyberthreats

The increasing number of attacks and the growing complexity of cyberthreats are being compounded by a continuous shortage of cybersecurity talent. To address the estimated global shortfall of over 3 million cybersecurity professionals, there has to be 89% employment in the field. With AI, this gap can be easily covered.
Accelerated threat detection was one of foremost uses of AI in cybersecurity. AI can enhance the existing attack surface management techniques while reducing noise and activating the limited number of security professionals to concentrate on the most prominent signals and indicators of compromise. In addition to this, AI can make decisions and act more swiftly, permitting security teams to pay attention to more strategic tasks.
Advanced analytics and machine learning platforms can process the large amounts of data generated by security tools, assess data from the newly connected assets flooding the network. These platforms can be trained to differentiate between malicious files, devices, connections and users.
AI-driven platforms for asset mapping and networking offer real-time insights into an organization’s expanding attack surface. They can recognize and bifurcate active assets, including containerized ones, offering visibility into wretched asset behavior. In addition to this, AI-Powered supply chain risk management software can automate the monitoring of both digital and physical supply chain environments, and track how assets are interconnected and structured.
Cybersecurity Monitoring Tools and Techniques: The Essential List
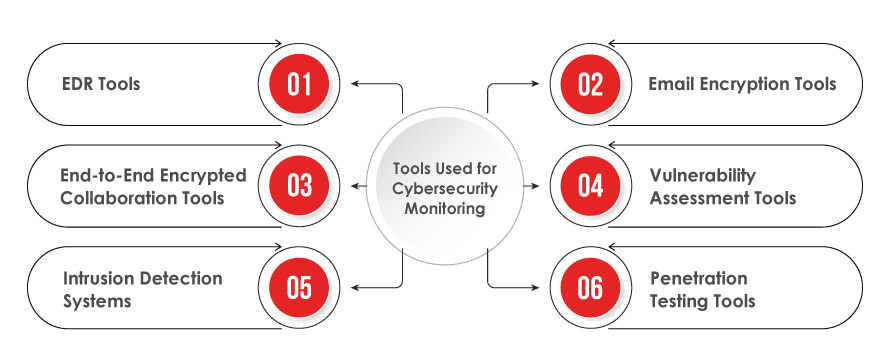
Here is a list of the most important cyber threat monitoring tools that every security-conscious organization need to consider in 2024:
Security Information and Event Management (SIEM) Systems:
SIEM systems are important to a robust cybersecurity monitoring strategy, offering real-time analysis of security alerts from network hardware and applications. This helps in quick detection and mitigati0on of potential threats.
Tools Used for Cybersecurity Monitoring:
EDR Tools:
These tools serve as guards for network endpoints like mobile devices, laptops, and servers. They collect the data and look for indicators of compromise, like suspicious IP addresses or URLs.
Email Encryption Tools:
These tools make sure that the content of your emails remains confidential and can be accessed by the intended recipients only. This helps reduce the risk and impact of data leaks and breaches.
End-to-End Encrypted Collaboration Tools:
There are tools to ensure that data is encrypted at the sender’s end and remains encrypted until it reaches the required recipient, protecting the confidentiality and integrity of data in remote working environments.
Vulnerability Assessment Tools:
At Tx, we use Tx-Secure for identifying, prioritizing, and quantifying vulnerabilities in an organization’s systems. Continuous scanning helps businesses proactively address potential threats before they can be exploited.
Intrusion Detection Systems:
IDS regularly monitors network traffic for malicious activity and signs or policy violations, alerting system administrators to suspicious events so that they can intervene promptly and safeguard breaches.
Penetration Testing Tools:
These tools are used to regulate ethical hacking exercises by simulating cyberattacks on a system. This permits organizations to recognize security misconfigurations and vulnerabilities, strengthening their overall security posture.
Conclusion:
AI and humans have been working in collaboration to detect and prevent breaches for some time. Though many organizations are in the early stages of adopting Cyber AI, exposure and attack surfaces beyond traditional enterprise networks continue to expand, AI offers even better potential.
Techniques like machine learning, natural language processing, and neural networks can help security analysts in differentiating between significant threats and irrelevant noise. By leveraging pattern recognition, supervised and unsupervised ML algorithms, and predictive and behavioral analytics, AI can help detect and thwart attacks, identifying abnormal user behavior, unusual allocation of network resources, or other anomalies.
AI can be deployed to secure on-premises infrastructure and enterprise cloud services, though securing resources and workloads in the cloud is generally less complex than in legacy on-premises environments.
While AI or any technology alone cannot solve the complex security challenges, its ability to learn and identify patterns in real time can accelerate detection, response efforts and containment. AI can reduce the burden on Security Operations Center (SOC) analysts allowing them to be more proactive. With this. The role of professionals in demand will decrease, saving on costs.
Discover more
Get in Touch
Stay Updated
Subscribe for more info




