
Application Security Services
Safeguard your Digital Frontiers with a Proactive and Comprehensive Approach
Talk to our ExpertsVulnerabilities in applications can lead to severe data breaches, loss of customer trust, and significant financial repercussions. Our Application Security Services provide an essential shield, safeguarding your applications from potential threats. We employ security testing, including penetration testing and vulnerability assessments, to identify and rectify security flaws. By integrating security measures from the early stages of application development, we ensure a robust, secure product.
Business Value Delivered
Get In Touch- Significant decrease in the risk of data breaches and cyberattacks
- Improved application functionality and reliability
- Enhanced compliance and regulatory adherence
Benefits of Securing Your Business Applications
Unifies Processes and Technologies
Strategically infuses security into every stage of the development lifecycle through careful planning, design, implementation, integration, and deployment.
Increases Regulatory Compliance, Quality and Cost Reduction
Encourages the implementation of “shift-left” techniques to identify and address security flaws in applications at an earlier stage of the Software Development Life Cycle (SDLC).
Securely Accelerates Innovation and Development
Facilitates the automation and incorporation of security measures within the continuous integration and continuous deployment (CI/CD) pipeline.
Secured with Center for Internet Security (CIS)
Renowned for its best-in-class security benchmarks, CIS offers a secure roadmap for your applications, minimizing risk, enhancing compliance, and deterring even the most cunning errors.

Speak to an expert
In your line of work, we know every minute matters.
Our Application Security Services
Proactive Vulnerability Management
We check for vulnerabilities in real-time using ethical application security techniques. It includes implementing automated scans to identify known weaknesses in your code and infrastructure.
Data Protection and Compliance
Implement controls to prevent unauthorized access, exfiltration, and misuse of sensitive data.
DevSecOps Integration
Embed security practices throughout your development lifecycle, reducing vulnerabilities and future remediation costs. It involved utilizing automation and integration to streamline security testing and feedback within your CI/CD pipeline.
API & Container Security
Protect your application programming interfaces (APIs) from unauthorized access and attacks while securing your containerized applications and microservices with specialized tools and best practices.
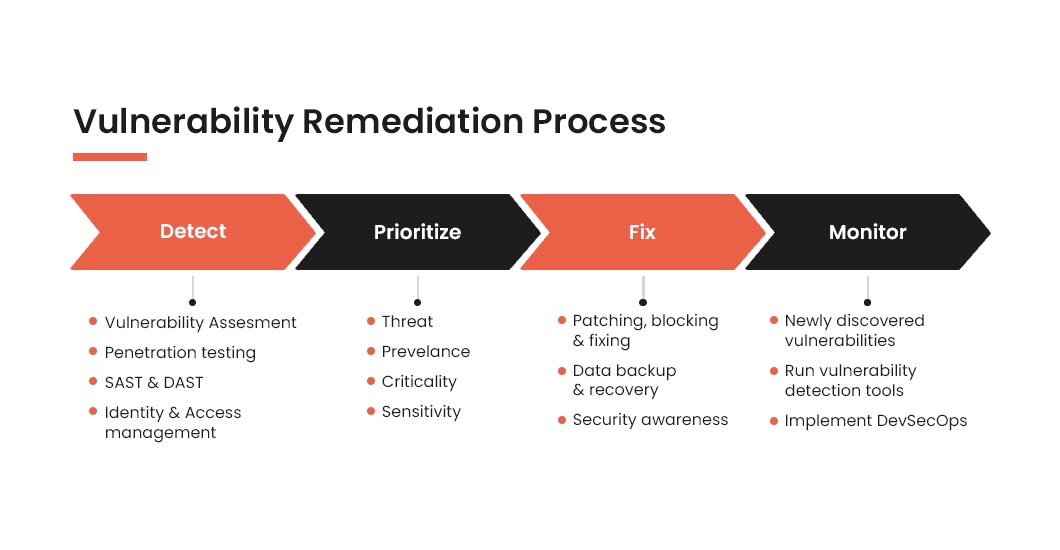
Tx's Vulnerability Remediation Process
Our application security focuses on identifying, prioritizing and resolving security vulnerabilities from the outset, saving both effort and substantial costs.
Our Application Security Differentiators
Leveraging industry leading best practices and standardized frameworks to deliver effective security assessments and penetration test
Ensuring targeted and effective approach to mitigate risks.
Leveraging automation to improve efficiency and accuracy.
Integrating security early on, minimizes delays and expedites time to market for secure applications.
