- What is Hashing in Cybersecurity?
- The Role of AI in Enhancing Hashing Techniques
- AI and Quantum-Resistant Hashing: Preparing for the Future
- The Importance of Hashing in Zero Trust Architectures
- The Role of AI-Powered Hashing in Compliance
- How Tx Can Help You Implement AI-Powered Hashing for Cybersecurity
The recent cyberattacks targeting critical infrastructure have witnessed the use of advanced methods to break traditional encryption and hashing techniques. The traditional hashing algorithms like MD5 and SHA-1, once reliable, are now susceptible to more sophisticated, AI-driven attacks – Microsoft Security Report, 2024.
This development has resulted in the innovation in the cybersecurity space, with AI-Powered hashing algorithms coming out as a promising solution. The use of AI in cybersecurity has moved beyond the basic automation to intelligent learning, predicting threats and adapting encryption techniques in real-time. As the digital world grows more complex, the need for AI-driven hashing has never been more pressing.
The Growing Threat to Traditional Hashing
As computing power advances and threats become more sophisticated, traditional hashing methods are increasingly vulnerable to brute-force attacks and collision attacks.
The rise of quantum computing and AI-enhanced cyberattacks has multiplied these risks. Hashes that were once impossible to reverse-engineer, are now at the risk of being cracked, revealing sensitive data to unauthorized access. To overcome these threats, AI-Powered hashing techniques are coming up as the next wave of encryption, offering dynamic and adaptive solutions for securing data in real-time.
What is Hashing in Cybersecurity?
Before diving deeper into how AI is changing the hashing, it is important to understand what hashing is and why it is important. Hashing is the process that converts an input (e.g. a password or file) into a fixed-length string of characters, specifically a hash value or digest. This is done using hashing algorithms like SHA-256 (Secure Hash Algorithm) and MD5 (Message Digest Algorithm). Unlike encryption, whatever is reversible, hashing is a one-way process designed to protect data integrity.
Some of the key uses of hashing include:

Data Integrity:
Hashing makes sure that files or messages haven’t been adjusted during transmission by comparing the hash value before and after transmission.
Password Storage:
Passwords are hashed before being stored in databases to safeguard them from exposure in the event of a data breach.
Digital Signatures:
Hashing helps verify the authenticity of digital signatures, making sure that the data is not tempered with.
However, with the rise of advanced attack methods, like rainbow table attacks and collision attacks, traditional hashing is no longer enough to ensure security. This is where AI comes in.
The Role of AI in Enhancing Hashing Techniques
As attackers take advantage of AI to crack traditional hashing methods, AI-driven defenses are becoming more critical. Here’s how AI is transforming the game for hashing in cybersecurity:
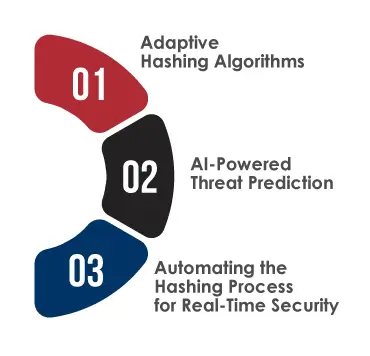
1. Adaptive Hashing Algorithms
AI allows the development of adaptive hashing algorithms, which can change and improve over time on the basis of the types of attacks they encounter. Unlike traditional static algorithms, AI-Powered hashing systems can identify and learn from patterns in cyberattacks, dynamically adjusting the hashing process to safeguard exploitation.
For example, machine learning models can be trained to detect vulnerabilities in hashing algorithms by analyzing patterns in how hashes are cracked. This predictive approach enables AI systems to foresee and counter new types of attacks before they become widespread.
2. AI-Powered Threat Prediction
One of the most powerful capabilities in cybersecurity is its ability to predict potential threats by examining historical attack data and detecting emerging patterns. When applied to hashing, AI systems can detect when a hashing algorithm is under threat from techniques like brute-force attacks or collision generation.
For instance, AI can analyze attempts to generate different hash values from a single source, anticipating an impeding collision attack and adjusting the hashing algorithm as required to prevent vulnerabilities. This proactive threat detection is critical for businesses handling sensitive data like financial transactions, intellectual property and personal information.
3. Automating the Hashing Process for Real-Time Security
AI is also being used to automate hashing processes in real-time, eradicating the potential for human error and refining response times. Automating complex hashing algorithms through AI eliminate the risk of misconfigurations and ensures that even the most advanced security protocols are implemented regularly.
This level of automation is specifically beneficial in industries that handle large-scale data transactions, like financial services and healthcare, where the accuracy and speed of hashing processes are crucial for maintaining security.
AI and Quantum-Resistant Hashing: Preparing for the Future

With the arrival of quantum computing, traditional cryptographic hashing methods face even greater threats. Quantum computers have the potential to break common hashing algorithms much faster tha classical computers, putting the sensitive data at risk.
AI is already being positioned to develop quantum-resistant hashing algorithms, capable of withstanding the computational power of quantum machines. These AI-Powered algorithms use complex mathematical models to create hash functions that are resistant to quantum attacks. The most advanced AI systems are being used to simulate quantum computing environments and anticipate how future cyberattacks might exploit quantum computing environments and predict how future cyberattacks may exploit quantum technologies, enabling researchers to design more secure hashing methods.
Example: AI-Driven Quantum-Resistant Hashing in Cryptocurrency
One notable application of AI-Powered, quantum-resistant hashing is in the world of cryptocurrencies like Bitcoin and Ethereum. Cryptocurrency platforms are highly dependent on hashing for transaction validation and security; however, the rise of quantum computing poses a major threat to the integrity of these systems. AI is being used to develop post-quantum cryptographic solutions, ensuring that cryptocurrency networks remain secure in the future where quantum attacks become feasible.
The Importance of Hashing in Zero Trust Architectures

As there is a tremendous growth in the adoption of Zero Trust Security Models, hashing plays a crucial role in verifying identities and ensuring data integrity. In a Zero Trust architecture, every access request is treated as if it originated from an untrusted source, meaning regular authentication and validation are required.
AI-enhanced hashing can improve the effectiveness of Zero Trust models by dynamically validating user identities and ensuring that data integrity checks are performed in real-time. This enables businesses to enforce the security protocols without any leakage in performance or user experience.
The Role of AI-Powered Hashing in Compliance
For organizations operating in strictly regulated industries, like finance, healthcare, and eCommerce, maintaining compliance with data protection standards is crucial. Regulations like HIPAA, GDPR, and PCI DSS need organizations to use encryption and hashing to protect sensitive data.
AI-Powered hashing algorithms offer an extra layer of security, assisting businesses to maintain compliance by automatically adjusting to the latest cybersecurity threats. This makes sure that organizations can stay ahead of attackers while meeting their regulatory obligations.
How Tx Can Help You Implement AI-Powered Hashing for Cybersecurity

At Tx, we understand the evolving nature of cybersecurity and the importance of using AI-driven technologies to protect sensitive data. Through our Tx-Accelerator platform, we assist businesses implement AI-Powered hashing algorithms that accelerate security, improve efficiency, and maintain compliance with industry standards.
Our cybersecurity advisory services pay attention to helping businesses stay ahead of emerging threats. Be it upgrading your existing encryption protocols, securing your blockchain infrastructure, or adopting a Zero Trust model, we have the expertise to guide you through the process.
Conclusion: Embracing the Future of Hashing with AI
With cyberattacks becoming more sophisticated, traditional hashing methods are no longer enough to protect sensitive data. AI-Powered hashing represents the future of encryption, offering automated, adaptive, and quantum-resistance solutions that keep businesses secure in a complex digital landscape.
By embracing AI-enhanced hashing techniques, organizations can safeguard their data, comply with industry standards, and stay ahead of the recent threats. Ready to upgrade your cybersecurity infrastructure with AI-Powered solutions? Get in touch with Tx to learn how we can help you stay secure in the dynamic world.
Discover more
Get in Touch
Stay Updated
Subscribe for more info