
- Information Security Management System
- Why do Businesses Require ISMS?
- 5 Key Benefits of Implementing ISMS
- Best Practices for Setting Up ISMS
- How can Tx help with ISMS Implementation?
- Summary
Today’s business ecosystems are data-driven, making protecting sensitive information and other digital assets across industries critical. As the tech landscape rapidly evolves with the involvement of AI, ML, cybersecurity, edge computing, VR, etc., businesses face the ever-increasing risk of cyber threats. These threats damage brand reputation, compromise sensitive data, and hamper business operations. That’s why it is a high priority for enterprises to have security practices in place to protect their digital assets, ensure legal compliance, and maintain a competitive edge. But how can this be done? The answer is “implementing an information security management system (ISMS).”
Information Security Management System

According to a report cybersecurity and cybercrime are ranked 8th in the biggest global risk list based on severity. It also states that the tech gap will worsen while cybersecurity risks continue to rise. An information security management system is a systematic approach allowing businesses to manage their information security infrastructure. By implementing ISMS, businesses can ensure their data’s availability, confidentiality, and integrity. It consists of procedures, controls, and policies that enterprises can utilize to manage risks associated with data security. This involves internal errors, cyberattacks, data vulnerabilities, etc. ISMS key aspects include:
- Identify threats and vulnerabilities impacting information security
- Implement technical, administrative, and physical controls to control risks
- Regular monitoring and improving systems to handle evolving threats and regulatory requirements
- Ensuring compliance with legal and industrial standards like PCI DSS, ISO/IEC 27001, etc.
Why do Businesses Require ISMS?

An ISMS offers enterprises a comprehensive overview of their information security ranking and what tools they need to maintain or strengthen their security protocols. Consider data a castle surrounded by thick walls to protect its valuable content from unethical access. ISMS can strengthen those walls by implementing periodic checks to secure assets and keep them up-to-date per security measures. It offers several benefits to organizations:
- It ensures information risk stays within the ratio that an enterprise can handle.
- Organizations can identify and proactively address threats and vulnerabilities in a structured manner.
- By ensuring compliance with ISMS standards like ISO/IEC 27001, companies can strengthen their information security while fulfilling regulatory requirements like GDPR, NIS2, etc.
- Businesses can ensure the confidentiality, availability, and integrity of their users’ data.
- Businesses can avoid heavy penalties for not meeting regulatory requirements and prevent financial losses associated with breach recovery.
5 Key Benefits of Implementing ISMS

The benefit of the information security management system is that it can protect businesses against cyberattacks by establishing controls that tackle attack risks. Let’s take a quick look at some of the benefits of implementing ISMS:
Information Security in All Forms
Enterprises can establish a comprehensive framework consisting of procedures, processes, policies, and controls to protect all forms of information. The protection covers data at rest, in transit, and in use. For example, under GDPR, businesses must secure personal information, a requirement that a good ISMS implementation would strictly address. It also allows enterprises to classify their data and implement adequate security measures.
Preventing Loss of Reputation
Budgets are limited while cybercrime is rising, and businesses require strict protection against data loss and fines associated with not complying with regulations like GDPR and HIPAA. By implementing ISMS, businesses can establish security protocols to reduce intrusions, improve security measures, and minimize the financial impact of breaches. For example, GDPR authorizes entities like ICO to impose fines of up to €20 million or 4% of annual turnover for data protection violations. Implementing an ISMS can help businesses prevent such hefty fines and maintain brand credibility and customer trust.
Promoting Safety
Implementing ISMS represents a fundamental shift towards safety and accountability. This step is crucial as human factors are the leading cause of data breaches. ISMS helps promote regular training, assessments, and auditing to enhance security practices and promote a culture of responsibility. This helps mitigate risks related to insider threats and human errors, thus optimizing overall enterprise security.
Swift Response to Evolving Threats
Cyber threats are constantly evolving and becoming more sophisticated. This is why it is becoming difficult for businesses to respond effectively whenever a security incident occurs. Information security management system allows enterprises to anticipate future needs and address external and internal threats while adapting to changes. With proactive risk mitigation measures, businesses can protect their valuable data and systems while ensuring safety and compliance. They can avoid possible threats and internal risks so they can never be caught off-guard.
Improving Customer Trust
Data privacy concerns are understandable in the current tech-driven era. Thus, having ISMS in place will show the company’s commitment to information security, which helps improve customer and end-user trust. By leveraging standards like ISO/IEC 27001 and GDPR, companies can put themselves in a positive light in the market, thus improving customer loyalty and attracting new business opportunities.
Best Practices for Setting Up ISMS
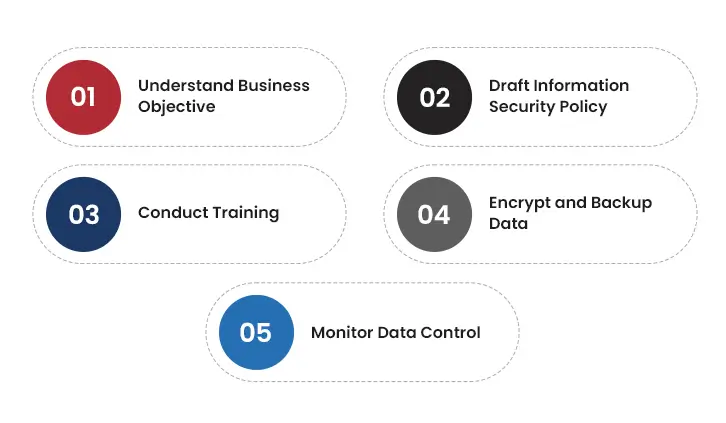
The ISO 27001 and 27002 standards have defined best-practices guidelines for enterprises to set up an information security management system. Let’s take a look at the checklist to consider when considering ISMS implementation:
Understand Business Objective
To understand the business objectives, organizations must get a clear picture of the business operations, tools, technologies, and ISMS. They should also know what security goals one wants to achieve by executing an ISMS. By doing so, businesses would also know how the ISO 27001 framework can assist them with data protection and people who will handle ISMS execution.
Draft Information Security Policy
It would be best to have an information security policy before setting up an ISMS. This would allow the company to identify weak points in its policy, which will consist of an overview of the security controls within an enterprise.
Conduct Training
Businesses should conduct regular security awareness training for their employees. They should know about the evolving cyber threat ecosystem, common data vulnerabilities, and remediation and mitigation methods to secure data from breaches.
Encrypt and Backup Data
Data encryption can prevent unauthorized intrusion and be the best defence against cyber threats. It is important to encrypt all forms of data before setting up an ISMS. Also, backup protocols should be maintained to prevent data loss issues. Businesses should have a plan to keep backups safe and secure on-premises and in cloud storage.
Monitor Data Control
Businesses should monitor their data access control policies and ensure that only authorized users can access critical information. They should observe who is accessing what, when, and where, along with tracking login and authentication.
How can Tx help with ISMS Implementation?

A clear picture of threats and risks to your information systems will help you take effective and measurable action. However, setting up an information security management system requires much time, documents, and detailed data analysis. Partnering with Tx would help you streamline the entire ISMS implementation process, from policy creation to security controls mapping and identifying security gaps. Our services cover the following:
Advisory & Consulting
We conduct detailed analyses and offer ISMS advisory and consulting to determine what security controls your organization requires. Our security experts will analyze your business infrastructure, covering compliance, industry standards, and security measures, to offer you the best advice for the following steps.
ISMS Implementation
We assist in implementing controls (physical, administrative, and technical) to implement an information security management system seamlessly. This ensures that everyone within the enterprise, including sensitive information and IT infrastructure, is protected.
Tx-Secure
Our in-house accelerator consists of processes and guidelines that assist businesses in overcoming cyber threats and vulnerabilities quickly and efficiently.
Summary
An Information Security Management System (ISMS) is crucial for modern businesses to protect sensitive data in an increasingly digital and vulnerable landscape. Implementing ISMS helps enterprises manage information security risks, ensuring data confidentiality, integrity, and availability. With the rise of cyber threats, businesses require robust security protocols to avoid breaches, financial losses, and non-compliance penalties.
ISMS offers comprehensive data protection, improved customer trust, and the ability to adapt to evolving cyber threats. By adhering to best practices and standards like ISO/IEC 27001, businesses can secure their digital assets and maintain compliance. Tx offers expert guidance in ISMS implementation, streamlining processes to safeguard company data. To learn how Tx can assist you, contact our experts now.
Discover more
Get in Touch
Stay Updated
Subscribe for more info




