In today’s connected IT world, cyber security is rapidly turning out to be more than just a technical issue. It has become explicitly essential for organizations to make sure that they have the right strategy in place to preempt any security attacks. A security breach when arises, cannot be undone completely and may leave you with the loss of data, damaged the reputation and legal consequence. Hence it is important that the subject is managed proactively by ensuring the robustness of your IT systems.
Cyber Security Testing Overview
Measures employed by enterprises to ensure data security:
– Using the correct security methods to detect and prevent security breaches at all levels
– Using firewalls as an attempt to limit all kinds of unauthorized access
– Using Analytics to detect any abnormal data usage activities which can also be used as a signal for an attack to occur
– Using a developed infrastructure for supervision, training, and technical support for teams with the responsibility of data management and data collection
– Using encryption for your sensitive data
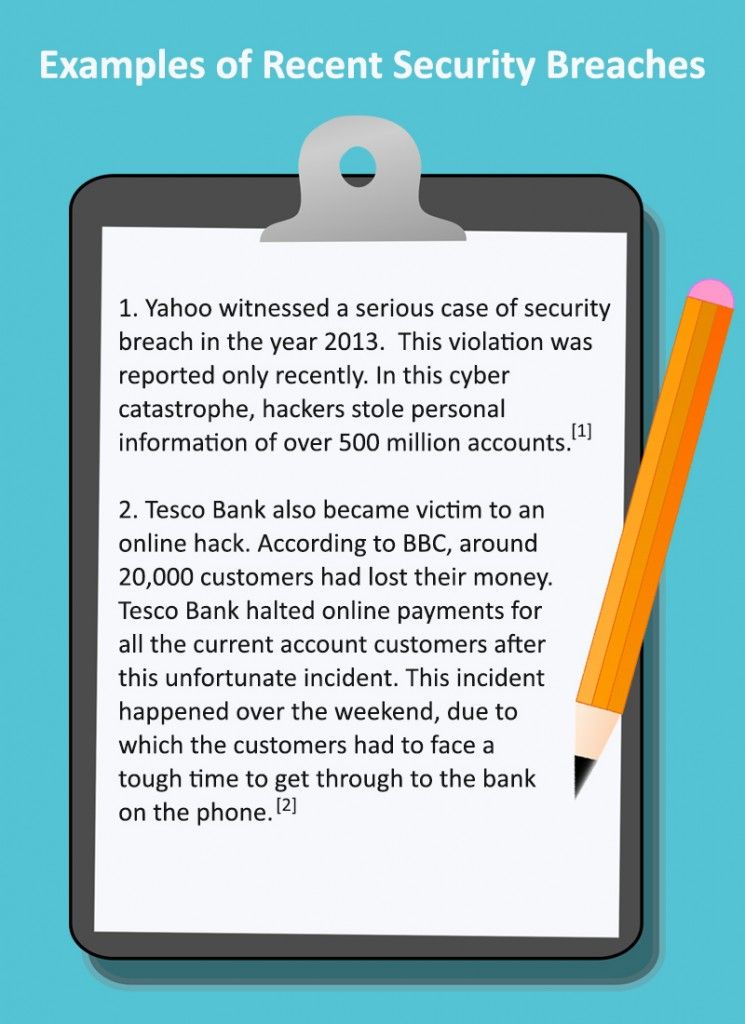
No one is safe – Data security issues have affected organizations of all sizes and technical caliber
Preventive Measures for Data Security
This old adage is as true for human health as for the IT systems of your organization. Humans take the time to recover from infections, and still they may not be able to recover fully, therefore it is important to prevent infections. Likewise, it is as important for an organization to keep its IT systems secure rather than just relying on a robust recovery process. The best method to avoid any issue is to make security the utmost priority for your organization.
The best practice to achieve this objective is to educate teams to be aware of data security best practices and trends. The technical teams should specifically focus on the new happenings and threats in the world of security and use the right set of tools to prevent various cyber attacks or threats. For example – Static Code Analyzers can help automate the process of detecting all kinds of vulnerabilities in the source code. It can further assist in identifying where open source code is used in the software using which vulnerabilities can be tracked and avoided.
Role of Security Testing
Security testing ensures that all IT systems in the organization are free from all kinds of vulnerabilities and weaknesses. Security testing process involves the evaluation of security risks within the systems under test and to highlight the security threats using various tools and techniques.
The security testing process consists of security scanning, vulnerability scanning, security review, security auditing, penetration testing, etc. In particular, security testing helps enterprises to ensure that their data is not exposed to any breach.
[BLOG] The Inevitable Need for #DataSecurity and How #Security #Testing Can Help?https://t.co/wWpz7t0WCW
— TestingXperts (@TestingXperts) January 2, 2017
At TestingXperts, we have a team of Certified Ethical Hackers (CEH) that can ensure that your systems are rigorously tested for all possible vulnerabilities. Our expertise in assessing a wide range of security threats allows us to be among the best security testing companies. We follow the Open Web Security Project (OWASP) guidelines along with with SANS, OSSTMM, HIPAA, SOX, WAHH, PCI-DSS, WASC, and NIST as per the client specific requirements.
Reference Links:
Discover more
Get in Touch
Stay Updated
Subscribe for more info