
- An Overview of Continuous Threat Exposure Management
- How does it work?
- What Problem is CTEM Solving for Businesses?
- 5 Stages of Continuous Threat Exposure Management Program
- Businesses with CTEM vs. Without CTEM
- Why Partner with Tx to Manage Cybersecurity?
- Summary
“A breach has occurred, and the company’s data has been compromised,” mentioned in the large bold letters in the newspaper’s headlines. Investors are in panic, the general public is worried, and the company’s CEO and CISO face all the backlash. But what if they had anticipated that kind of cyberattack with the help of CTEM beforehand? As digital transformation grows, the attack surface for enterprises also expands exponentially. The security teams have to manage an infeasible rate of vulnerabilities. According to Gartner, businesses prioritizing security investments per continuous threat exposure management strategies will suffer three times fewer security breaches.
Businesses have invested heavily in 2FAs, firewalls, breach detection, and other defense parameters for years. In addition, compliance concerns forced them to deploy vulnerability scanners and implement an aggressive approach with read teaming and anticipated breach practices. Although this strategy did address specific business needs, it still lacked something. Despite all these efforts, breaches still occurred, and businesses faced heavy financial and trust losses. We all know how Facebook has been a prime target of security incidents on multiple occasions. This is why businesses have shifted from a vendor-by-vendor approach to a more refined data consolidation approach. In fact, 75% of organizations are already pursuing security vendor consolidation. This shift is paving the way for a continuous threat exposure management approach.
An Overview of Continuous Threat Exposure Management

CTEM is a proactive cybersecurity approach that facilitates continuous monitoring, evaluation, and mitigation of security vulnerabilities across an organization’s IT infrastructure. Generally, businesses rely on tools like AVs, XDRs, SIEMs, and MDRs to protect their organizations against cyberattacks. These tools are undoubtedly crucial, but they follow a reactive approach. They will only act after an attack is in action. Businesses might believe they are well-protected using these tools until they perform a thorough offensive security check. In the current digital age, it is important to consider more proactive approaches like attack surface management, pen testing, and CTEM programs as they focus on being offensive rather than defensive.
Continuous threat exposure management allows businesses to identify and mitigate weaknesses in their processes. It involves analyzing the environment, identifying vulnerabilities, assigning priority according to risk, marking attack paths and loopholes, and assigning teams to address them. By implementing the CTEM program, businesses can proactively resolve their security risks to stay one step ahead in this dynamic threat landscape.
How does it work?
At its core, CTEM uses automated tools to scan vulnerabilities continuously across business digital assets. These tools integrate with security infrastructure to comprehensively view the organization’s threat ecosystem. After detecting the vulnerability, the CTEM program assigns priority based on the potential impact, providing quick and effective remediation.
What Problem is CTEM Solving for Businesses?
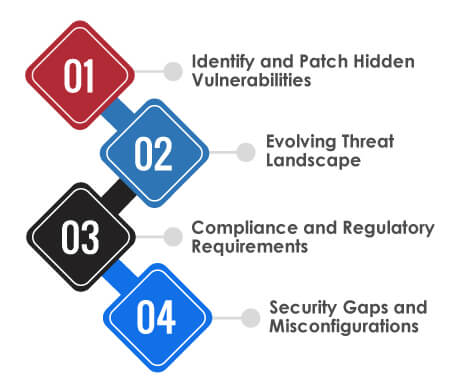
A continuous threat exposure management program allows CISOs and their teams to address critical pain points in the modern cybersecurity ecosystem, namely the gap between threat emergence and response. They continuously face relentless pressure to secure the organization’s critical data and infrastructure assets. Preventive measures like firewalls and AVs were once all they needed, but now, cyber-attacks are more persistent and sophisticated than ever. CTEM assists CISOs in addressing a valuable security gap by offering a comprehensive and on-the-run view of the business attack surface. Let’s take a close look at the problems that CTEM is solving for businesses:
Identify and Patch Hidden Vulnerabilities:
Vulnerabilities are discovered constantly, but sometimes, few remain unnoticed. CTEM program performs beyond point-in-time scans and facilitates continuous identification of these vulnerabilities. This assists security teams in prioritizing the patching process and mitigating the critical risks before they harm business.
Evolving Threat Landscape:
The cyber threat ecosystem is constantly evolving rapidly. CETM assists CISO in incorporating threat intelligence techniques to analyze and understand the latest attack methods. This would enable businesses to stay alert, anticipate potential attacks, and plan an effective mitigation measure.
Compliance and Regulatory Requirements:
With the evolving cyber-attack ecosystem, regulations have become stricter and more complex. It raises significant compliance concern for businesses. CTEM ensures that businesses maintain continuous compliance by keeping security protocols up to date with the latest regulations.
Security Gaps and Misconfigurations:
No matter how profound and robust policies businesses implement; misconfigurations and security gaps will remain. With CTEM, CISOs can constantly monitor the systems and configurations, enabling them to identify and mitigate security gaps before hackers can exploit them.
By addressing these problems, CTEM assists CISOs and their teams in enhancing the cybersecurity framework and supporting overall operational integrity. This makes CTEM a valuable asset for businesses to protect their digital assets against cyber threats.
5 Stages of Continuous Threat Exposure Management Program

The five stages of the CTEM program provide a comprehensive and cyclical overview of handling cybersecurity risks. Each stage allows businesses to constantly identify, assess, and mitigate cyber threats. The best part is these measures evolve as threats evolve, maintaining a robust defense mechanism. Let’s take a look at the five key stages of implementing the CTEM program:
Scoping:
The first stage requires security teams to identify the infrastructure segments to detect potential vulnerabilities or threats. They conduct a thorough analysis of cyber resilience using automated tools and sensors and check internal and external attack surfaces, as well as cloud infrastructure. The sensors monitor and collect data from all network and system components.
Discovery:
This phase involves an in-depth analysis of the infrastructure defined in the first stage. The security teams assess all assets to evaluate risk profiles and their potential impact on the business. They can find explicit vulnerabilities and detect hidden errors like misconfigurations and fake assets. The extensive data collected in this stage would allow security teams to prioritize their discovery efforts.
Prioritization:
This stage assists security teams with a gap analysis of security infrastructure. It involves identifying undetected/unprevented attacks, detection gaps, logging gaps, and broken, noisy, and missing detection rules. CISOs can focus on where they are most needed to prevent resource wastage on less critical issues.
Validation:
The security teams utilize various tools to validate the impact of identified loopholes. This phase is crucial to verifying a business’s cybersecurity protocols. It is followed by prioritizing weak points, threats, and mitigation processes. The actions include patching software, updating system configurations, and improving security protocols.
Monitoring:
After validation, security teams must continuously monitor the effectiveness of cybersecurity measures to ensure that no new threats have been detected. This ongoing monitoring is the core of the CTEM program that sets it apart from traditional security assessments. CISOs also get real-time insights into the organization’s security posture.
Businesses with CTEM vs. Without CTEM

Implementing a continuous threat exposure management program would allow businesses influenced by CISOs to manage and respond more effectively to cybersecurity threats. CISOs can leverage CTEM to facilitate real-time threat detection, risk management, and adherence to compliance, which are necessary components in today’s cyber threat ecosystem.
|
Aspect |
With CTEM | Without CTEM |
| Threat Detection | Real-time detection allows immediate response. | Detection is often delayed, increasing the risk of damage. |
| Incident Response | Rapid and informed response to threats. | Slower, reactive responses, and less effective. |
| Security Posture | Dynamic and adaptive to new threats. | Often static, lacking adaptation to evolving threats. |
| Cost of Security Breaches | Low cost due to early detection and remediation. | Higher cost of security breaches due to the potential for extensive damage. |
| Compliance | Ensure continuous compliance with regulations. | Irregular compliance management |
| Resource Allocation | Optimized resource allocation with automation prioritizing critical issues. | Often inefficient, with resources spread thin. |
| Overall Security | Enhanced security with fewer vulnerabilities. |
High chance of vulnerabilities leading to increased risk. |
Why Partner with Tx to Manage Cybersecurity?

Partnering with Tx to manage cybersecurity can transform how businesses address cyber threats, especially with a robust CTEM program. We can assist CISOs with advanced tools and strategies to enhance their organizations’ cybersecurity posture. Selecting Tx to manage your cybersecurity posture would give you the following perks:
• We have a team of highly certified security professionals with expertise in CISM, CISSP, CISA, CAP, and CEH, who ensure your security infrastructure is free from vulnerabilities.
• Our approach to the CTEM program ensures that your cybersecurity measures are proactive and keep your digital ecosystem one step ahead of potential threats.
• Our approach aligns with industry standards such as OWASP, PIC-DSS, HIPAA, SOX, OSSTM, WASC, WAHH, and NIST.
• We utilize advanced automation tools and in-house accelerators, such as Tx-Secure, to provide continuous monitoring a real-time threat detection necessary for maintaining a resilient security posture.
• We assist in optimizing resource allocation to ensure your most critical assets receive the highest level of protection. It significantly reduces costs associated with managing security threats.
Summary
Continuous threat exposure management is a crucial component for businesses if they want to stay protected in the evolving cybersecurity ecosystem. It has the potential to empower CISOs with real-time threat detection, proactive vulnerability management, and ensure regulatory compliance. They can seamlessly address the critical gap between threat emergence and response. The proactive and continuous nature of CTEM ensures that organizations can adapt swiftly to emerging threats, thereby maintaining a robust defense system and operational integrity. Partnering with Tx enhances these capabilities, providing advanced tools, expertise, and continuous support for a resilient cybersecurity strategy.
Discover more
Get in Touch
Stay Updated
Subscribe for more info




