The quality software delivery trends have changed significantly in the past few years. Businesses are investing in modern software engineering technologies to create new features, release faster, and deliver value to their end-users quickly. However, the manually driven security processes have failed to keep up with new software delivery trends. As businesses depend on software solutions, the need to swiftly deploy updates should balance with the need to secure sensitive data and systems. Only then would businesses be allowed to fight against growing cybersecurity threats. This is where DevSecOps comes into play, which helps maintain robust business security.
The global DevSecOps market, valued at $3.73 billion in 2021, is projected to reach $41.66 billion by 2030. The surge is due to increased cybercrime activities, which cost trillions of dollars worldwide. Such figures highlight the growing need to ensure security with DevSecOps implementation. It substantially benefits businesses by automating security within the development cycle and improving the speed and safety of software deployments. 96% of IT leaders believe they could benefit from automating security and compliance operations, which are core principles of DevSecOps. Moreover, the increase in the usage of AI/ML, cloud computing, and other automation technologies is making DevSecOps more crucial than ever.
Understanding DevSecOps Pipeline
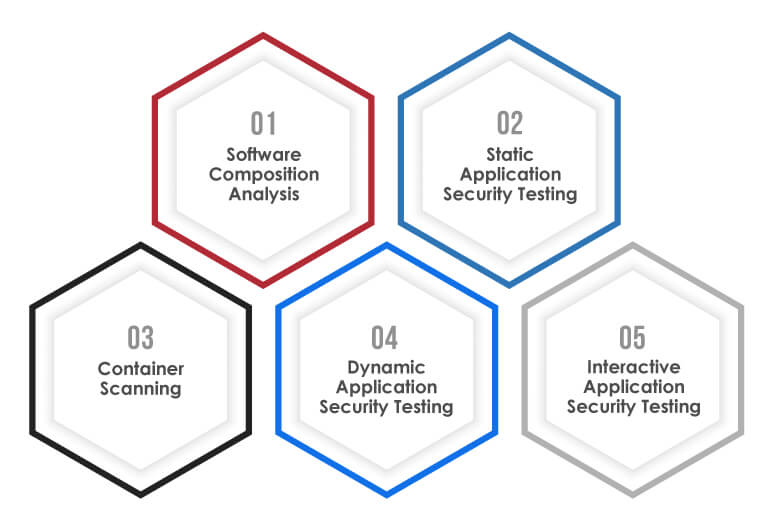
The DevSecOps or DevOps with Security pipeline integrates in every phase of software development. It ensures security protocols are embedded from the outset and not tacked on at the end. It also helps streamline workflows, reduce security vulnerabilities, and enhance software quality and security. Let’s take a look at DevSecOps pipeline stages:
Software Composition Analysis:
SCA scans open-source code used within the repositories to spot vulnerabilities. Organizations can detect open-source licenses that conflict with their software licensing policies. As many software contains open-source elements, SCA is a critical business process. In the DevSecOps pipeline, SCA runs the post-coding and implementation stage in the SDLC.
Static Application Security Testing:
After building the code and running SCA, businesses need to run SAST to scan the entire code base to identify defects, including OWASP’s Top Ten vulnerabilities. After SAST scanning, businesses can publish results and prevent the DevOps pipeline from continuing if security standards aren’t fulfilled.
Container Scanning:
This stage involves scanning container images to detect vulnerabilities. Software teams that use container orchestration platforms can run customer applications to verify whether containers are safe. This stage allows businesses to find bugs in the dependent libraries and base images and pinpoints changes in licensing. Container scanning is done after creating new container images and uploading them to a repository. If a vulnerability is detected in the image, the build will fail, and the image will not get uploaded to the repository.
Dynamic Application Security Testing:
After deploying the application to a test environment, DAST crawls the running app and attacks it like a rogue user. It allows businesses to detect issues like TLS and XSS certificate verification problems.
Interactive Application Security Testing:
IAST enables businesses to identify and manage security vulnerabilities discovered during runtime or dynamic testing. In this stage, businesses deploy sensors while the app runs to analyze interactions during manual and automated testing. It can detect encrypted data, file systems, and database access issues.
Role of DevSecOps in Optimizing Business Security
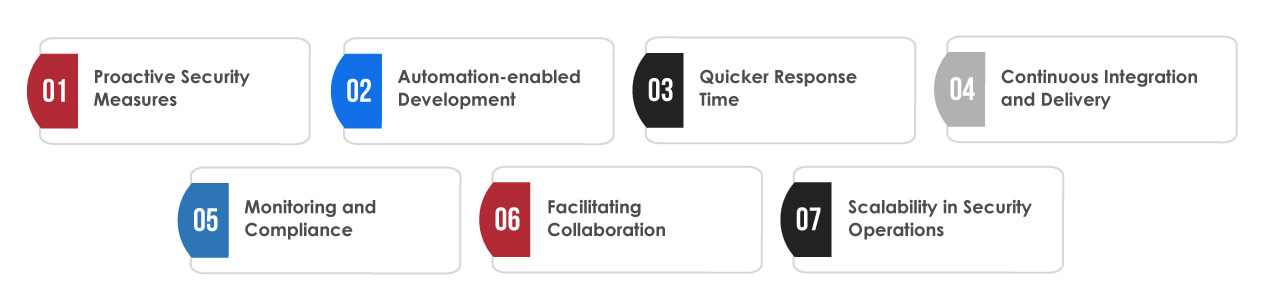
According to industry experts, not having DevSecOps may cause teams to overlook security protocols when it is urgent to deploy applications. It would also result in the deployment of potential vulnerabilities. DevSecOps integration ensures that security becomes a fundamental aspect of software development and operational processes. Businesses can instill the mindset that every organization member prioritizes security from the start, promoting a proactive approach, which is a core of DevSecOps culture. The following are some of the factors that define its role in ensuring business security:
Proactive Security Measures:
DevSecOps integrates security as a continuous, integral part of the SDLC. Incorporating security in the initial stages allows businesses to identify and mitigate vulnerabilities early on and prevent them from becoming a major hindrance. This proactive approach prevents security breaches before they occur.
Automation-enabled Development:
DevSecOps teams are professionals in syncing security testing with automated test suites, which help optimize operational efficiency. Businesses can leverage CI/CD pipelines to improve the automation of development and security processes and achieve higher effectiveness.
Quicker Response Time:
Security monitoring and testing are implemented throughout the DevSecOps pipeline to detect potential security incidents and address them quickly. This reduces the impact of security breaches and maintains business continuity.
Continuous Integration and Delivery:
The CI/CD process is the core of the DevSecOps pipeline. It facilitates the frequent integration of code changes into a shared repository. Every integration is further verified by an automated build and tests to detect errors. This ensures the software is developed, tested, and released quickly and has robust security integrity.
Monitoring and Compliance:
Continuous monitoring is another aspect of the DevSecOps pipeline. Monitoring tools continuously scan anomalies and security threats in the production environment. They ensure compliance with security standards and regulations by providing visibility into the application’s security posture.
Facilitating Collaboration:
To ensure business security with DevSecOps, businesses must ensure cooperation among teams with communication at its core. It helps resolve problems by sharing accountability among teams to achieve security goals.
Scalability in Security Operations:
As businesses grow, their security requirements also change. DevSecOps facilitates a scalable security framework to support businesses adapt to changing requirements without affecting the development process. Businesses can ensure rapid innovation while maintaining strict security standards.
DevSecOps Implementation Challenges
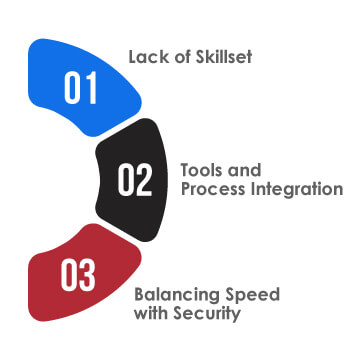
Implementing the DevSecOps methodology requires a change in cultural and organizational mindset, which can be a major challenge. Similarly, many other challenges are associated with implementing DevSecOps within the software development lifecycle. These challenges vary from cultural resistance to technical difficulties, affecting the integration process and DevSecOps’ effectiveness. The following are some common challenges associated with DevSecOps implementation:
Lack of Skillset:
DevSecOps requires a blend of development, security, and operational skills, which not every team member can initially fulfill. The shortage of DevSecOps professionals can hinder its effectiveness during implementation. This makes training and hiring new talent necessary, which adds to the complexity and cost of DevSecOps implementation.
Tools and Process Integration:
Integrating security tools and processes with the CI/CD pipeline is a technical challenge. It requires selecting tools and configuring them to work seamlessly with existing development and deployment processes. In addition, one must ensure that it does not cause disruption or system slowdown. This whole ordeal requires significant expertise and effort.
Balancing Speed with Security:
DevSecOp aims to integrate security without affecting delivery speed. Finding the right balance can be difficult. Adding security protocols and checks can slow down the development process, as it takes time to maintain speed and security and optimize the workflow.
Top 5 DevSecOps Best Practices
Implementing DevSecOps can enhance an organization’s security structure by integrating security practices in development and deployment processes. Following are the top 5 DevSecOps best practices that businesses should know about:
Setup DevOps Security Model:
The primary step in integrating the DevSecOps model is to incorporate cybersecurity measures, IAM (identity and access management), configuration, code review, and governance protocols within DevOps security tools. Implementing security in various DevOps security best practices pipelines makes it easy for businesses to release secure products. It also reduces the possibility of glitches, bugs, and recalls after product release within the DevSecOps process.
Security Process Automation:
To keep up with rapid development cycles without affecting security, businesses should automate tasks like vulnerability scans, security testing, and compliance checks. Automation will allow businesses to maintain high-security standards, enabling real-time threat detection and response without compromising development speed.
Conduct Regular Training:
Promote security culture within the organization by conducting training sessions and facilitating security awareness among all team members. Businesses must educate developers and operations teams about the latest security trends and threats to prevent security breaches and enhance project security.
Regular Security Audits:
Conduct regular audits of security measures and practices to ensure effectiveness and compliance with the latest security trends and technologies. Businesses can implement regular updates to security tools, libraries, and practices to protect against new and evolving cyber threats.
Implement Segmentation Strategy:
Another way to ensure the success of DevSecOps implementation is by avoiding hackers and attackers through segmentation. It is also known as the divide-and-conquer strategy. In this practice, businesses must limit access to app resource servers and address issues via continuous workflow. The network is divided into various segments, making it difficult for hackers to access data illegally. This DevSecOps technique enables businesses to prevent cyber threats and keep the error rate negligible.
Summary
DevSecOps integrates security within the SDLC and enhances the safety and security of software deployments. Due to the rise in frequency and complexity of cyber threats, this methodology has become crucial in software development. By embedding it into the early stages of development and automating security tasks, DevSecOps allows businesses to maintain robust security standards. Regular audits, a strong culture of security awareness, and continuous training sessions are vital for successful implementation. Businesses should partner with professional DevSecOps experts like Tx to ensure security keeps pace with their rapid development cycles.
How can Tx help with DevSecOps Implementation?

Tx offers exhaustive security analysis supported by comprehensive dashboards and reports. Our expertise in security testing for web apps, mobile apps, web services, and software products makes us the software QA and digital engineering industry leader.
• Our security experts understand that DevOps is a mindset and cultural change that includes collaborating operations and development teams into a seamless, agile process.
• We utilize our in-house accelerators, Tx-DevOps and Tx-DevSecOps, developed by the Tx Test Center of Excellence (TCoE), for digital businesses to reap benefits concerning code security.
• We aim to optimize your apps’ security within the existing DevOps CI/CD pipeline and ensure secure code deployment.
• Our accelerator, Tx-DevSecOps, automates the DAST process to determine runtime security issues before test deployment, enabling robust and continuous security testing within the DevOps CI/CD pipeline.
To know more, contact our QA experts now.
Discover more
Get in Touch
Stay Updated
Subscribe for more info