
In the digital age, data breaches pose a significant threat to organizations and individuals alike, with far-reaching consequences. However, recent technology trends are providing powerful tools and strategies to mitigate these risks and enhance data security.
According to recent statistics, the adoption of advanced technologies has shown promising results in data breach prevention. For instance, a study by Gartner revealed that by 2024, organizations leveraging artificial intelligence (AI) and machine learning (ML) for data security will experience a 30% reduction in data breaches. Additionally, research conducted by IBM found that companies employing encryption extensively reduced their financial impact by an average of $360,000 per data breach incident.
These statistics highlight the importance of embracing the latest technology trends to fortify defenses against data breaches and protect sensitive information in the digital landscape.
In this blog, we delve into the alarming rise of data breaches, the impact, and the urgent need for robust cybersecurity measures used in today’s interconnected world.
Importance of Securing Your Data from Breaches

In an era where cyber threats continue to proliferate at an alarming rate, reevaluating and fortifying our security paradigms has become imperative. In 2020 alone, the global cost of cybercrime reached a staggering $1 trillion, with businesses experiencing an average of 65,000 attempted cyber-attacks per day.
As per recent statistics, revealing an exponential surge in cyberattacks—over 300 billion malware incidents reported in 2022 —our traditional security measures are proving inadequate. The current landscape of cyber threats and their potential impact on organizations makes it the right time to invest in recent technological trends for cybersecurity. Cybercriminals have exploited vulnerabilities, resulting in a 600% increase in phishing attacks. These statistics highlight the urgency of investing in a digital immune system that can provide real-time threat detection, incident response, and proactive defence mechanisms. By investing now, organizations can strengthen their security posture, minimize the risk of breaches, and protect their valuable assets and data from growing cyber threats.
Different Types of Data Breaches
Several different types of data breaches can occur in the digital age. Here are some of the most common ones:
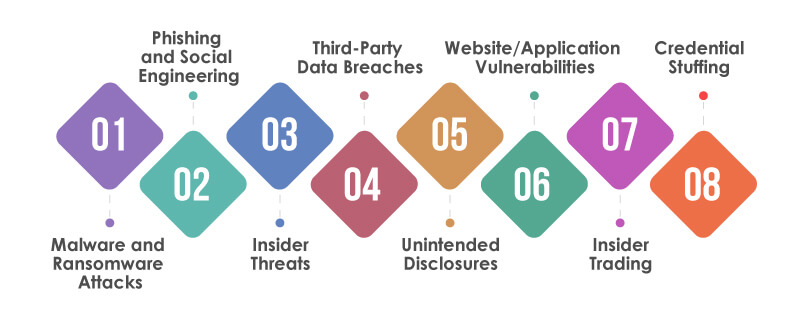
Malware and Ransomware Attacks:
Malicious software (malware) is designed to infiltrate computer systems and networks, compromising sensitive data. Ransomware, a type of malware, encrypts data and demands a ransom for its release.
Phishing and Social Engineering:
Phishing involves tricking individuals into revealing sensitive information, such as passwords or credit card details, by posing as a trustworthy entity. Social engineering manipulates human psychology to deceive individuals into sharing confidential data.
Insider Threats:
Data breaches can be caused by individuals within an organization who have authorized access to sensitive information. These insiders may intentionally or accidentally leak or misuse data.
Third-Party Data Breaches:
When organizations share data with external parties, such as vendors or service providers, there is a risk of those parties experiencing a data breach, potentially exposing the shared information.
Unintended Disclosures:
Unintentional disclosures can happen when sensitive information is mistakenly shared through email, fax, or other communication channels.
Website/Application Vulnerabilities:
Weaknesses or vulnerabilities in websites or applications can be exploited by hackers to gain unauthorized access to databases or user information.
Insider Trading:
In financial markets, data breaches can involve unauthorized access to non-public information, allowing individuals to gain an unfair advantage for personal financial gain.
Credential Stuffing:
This occurs when attackers use stolen username and password combinations from one breach to gain unauthorized access to other accounts, exploiting individuals who reuse passwords across multiple platforms.
The Impact of Data Breaches in the Digital Age
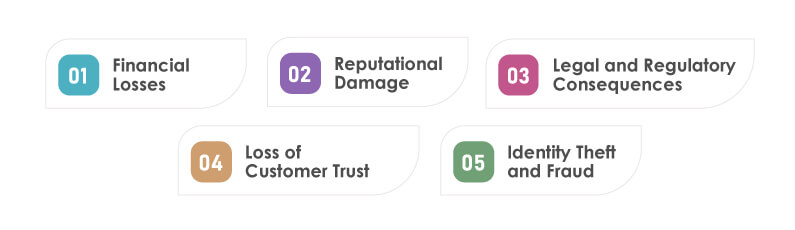
Data breaches in the digital age can have significant impacts on individuals, organizations, and society as a whole. Some of the key impacts include:
Financial Losses:
Data breaches can result in substantial financial losses for organizations. These losses can stem from various factors, such as legal fines, regulatory penalties, remediation costs, legal settlements, and damage to the organization’s reputation. Moreover, businesses may experience a decline in customer trust, leading to reduced revenue and potential loss of customers.
Reputational Damage:
Data breaches can severely damage the reputation of organizations. When sensitive data is compromised, customers may lose trust in the affected organization’s ability to protect their personal information. Negative publicity and public perception can have long-lasting consequences, making it challenging for the organization to regain its reputation and credibility.
Legal and Regulatory Consequences:
Data breaches often trigger legal and regulatory implications. Depending on the jurisdiction, organizations may face lawsuits, investigations, and fines for failing to adequately protect customer data or for violating data protection regulations. Compliance with regulations like the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA) is crucial to avoid legal consequences.
Loss of Customer Trust:
Data breaches can erode customer trust, resulting in a loss of loyalty and potential customers. Individuals whose personal information has been compromised may feel betrayed and reluctant to continue their relationship with the affected organization. Rebuilding trust can be a lengthy and challenging process, requiring transparent communication, enhanced security measures, and a demonstrated commitment to data protection.
Identity Theft and Fraud:
In many data breaches, personal and financial information is compromised, putting individuals at risk of identity theft and fraudulent activities. Cybercriminals can exploit stolen data for various purposes, including opening fraudulent accounts, conducting financial transactions, or impersonating individuals. Victims of identity theft may suffer financial losses, damage to their credit history, and the need for extensive remediation efforts.
How Latest Technology Trends Can Mitigate Data Breaches?
Mitigating data breaches requires staying ahead of evolving technology trends. The latest technology trends offer valuable tools and approaches to enhance data breach mitigation efforts. Here is how these recent technology trends can help alleviate data breaches:
Applied Observability Protecting Data Breaches

Applied observability plays a crucial role in mitigating data risks by providing organizations with comprehensive visibility into their systems and applications. By actively monitoring and collecting real-time data from various sources, organizations can detect and respond to potential data breaches or unauthorized access attempts promptly. Applied observability enables early detection of anomalies and abnormal data patterns, allowing organizations to take immediate action to mitigate risks.
It also enhances incident response capabilities by providing a holistic view of the digital ecosystem, enabling teams to trace and analyze the flow of data and identify the root causes of security incidents. Additionally, applied observability facilitates robust security monitoring, helping organizations proactively identify and address potential vulnerabilities before they are exploited. Applied observability empowers organizations to make data-driven decisions, strengthen their security posture, and safeguard against data risks effectively.
Adaptive AI Protecting Data Breaches

Adaptive AI, in the context of data risk mitigation, can be instrumental in enhancing organizations’ ability to mitigate data risks effectively. By leveraging adaptive AI technologies, organizations can bolster their security measures in the following ways. Firstly, adaptive AI systems can continuously analyze vast amounts of data, including network traffic, system logs, and user behaviors, to identify patterns and detect potential security breaches or data risks in real-time. Secondly, adaptive AI can dynamically adapt and evolve its algorithms and models to stay ahead of emerging threats and evolving attack vectors.
This enables organizations to proactively detect and respond to new and sophisticated data risks. Additionally, adaptive AI can automate security processes, such as threat detection, incident response, and risk assessment, reducing the time and resources required for manual analysis and response. Adaptive AI can help organizations identify vulnerabilities in their systems and applications, providing recommendations for remediation and strengthening overall data security. By harnessing the power of adaptive AI, organizations can significantly enhance their ability to identify, prevent, and mitigate data risks in today’s rapidly evolving digital landscape.
AI Trust, Risk and Security System Protecting Data Breaches

By leveraging AI Trust, Risk, and Security systems, organizations can detect, prevent, and respond to data breaches effectively. Through machine learning algorithms, they continuously analyze vast amounts of data, including network traffic, system logs, and user behaviors, to identify patterns indicative of potential security threats. By monitoring in real-time, they can swiftly detect anomalies, unauthorized access attempts, or suspicious activities, allowing organizations to take immediate action to mitigate risks.
AI Trust, Risk, and Security systems also enable proactive risk assessment by leveraging predictive analytics to identify vulnerabilities and potential weak points in an organization’s digital ecosystem. They automate incident response processes, reducing response times and minimizing human error, while continuously learning and adapting to new threats. By harnessing the power of AI, these systems enhance organizations’ ability to protect sensitive data, strengthen their security defenses, and effectively mitigate the risk of data breaches in today’s complex and evolving threat landscape.
Digital Immune System Protecting Data Breaches

A Digital Immune system can play a crucial role in mitigating data breaches by providing proactive and adaptive security measures. It continuously monitors networks, systems, and data in real-time, employing advanced technologies such as machine learning, AI, and behavioral analytics. By establishing baselines of normal behavior, it can swiftly identify deviations and anomalies that may indicate a potential breach.
The Digital Immune system can autonomously detect and respond to threats, leveraging automated incident response capabilities to mitigate the impact of breaches. It can dynamically adapt and learn from new data and emerging threats, enabling it to stay ahead of evolving attack vectors. By mimicking the principles of the human immune system, the Digital Immune system enhances organizations’ ability to detect and respond to data breaches, significantly reducing the response time and minimizing the potential damage caused by such incidents.
Conclusion
The rapid advancements in technology have both facilitated and complicated our lives in the digital age. However, when it comes to data breaches and the protection of sensitive information, recent technology trends have proven to be invaluable in mitigating risks and safeguarding data. From the widespread adoption of encryption techniques to the implementation of multi-factor authentication and the rise of artificial intelligence in threat detection, organizations and individuals now have a wide array of tools at their disposal to combat data breaches.
It is important for businesses and individuals alike to stay abreast of these technological developments and leverage them effectively to create a secure digital environment. As we continue to navigate the ever-evolving landscape of cybersecurity, embracing these trends and harnessing their potential will be essential in safeguarding our data and preserving the trust we place in the digital realm.
How TestingXperts Can Help Mitigate Risks Using Recent Technology Trends in Testing?

TestingXperts is at the forefront of leveraging recent technology trends in testing to mitigate risks effectively. Through the adoption of test automation, TestingXperts enables faster and more comprehensive testing, reducing human errors and increasing test coverage. Additionally, by incorporating Artificial Intelligence (AI) and Machine Learning (ML) algorithms, our experts can analyze vast amounts of testing data, detect patterns, and predict potential risks, enhancing the accuracy of risk assessment.
The utilization of cloud-based testing services allows TestingXperts to simulate real-world scenarios, perform load testing, and ensure the application’s robustness and resilience against security threats. Furthermore, with expertise in IoT and mobile testing, we offer comprehensive testing services for IoT devices and mobile applications, ensuring their security and functionality. By embracing these recent technology trends, our key goal is to empower organizations to enhance software quality, and deliver reliable and secure solutions.
Q1: What are the main causes of data breaches in the UK?
The main causes of data breaches include weak passwords, improper security measures, software vulnerabilities, poor data management measures, and much more. Other causes include backdoor vulnerabilities, distributed DDoS, phishing, unencrypted data, lost or stolen devices, etc.
Q2: What are Data Breaches?
Data breaches occur when an unauthorized user accesses, steals, or discloses sensitive information, harming its integrity, availability, and confidentiality. It can occur accidentally or intentionally to steal data. Healthcare and financial organizations face severe consequences due to data breaches.
Q3: How to avoid data breaches?
Data breaches can cause severe financial losses, service disruption, and identity theft. Businesses must use strong encryption, conduct regular security audits, use strong encryption protocols, create a response plan, and implement secure authentication measures to avoid data breaches.
Q4: Why do you need to report data breaches?
Data breaches result in serious consequences that impact both organizations and associated personnel. Its reporting is necessary to comply with legal requirements, mitigate risks, prevent damage, protect individuals/organizations, and ensure transparency and accountability.
Discover more
Get in Touch
Stay Updated
Subscribe for more info




