
The rapid increase in cyber-attacks has made cyber security a major concern for businesses. Irrespective of business size, whether it is a startup, SMB, MNC, or the world’s leading enterprise, every business has the threat of possible cyber-attacks by hackers due to the vulnerabilities existing in their systems. Also, the new remote working culture due to the COVID-19 pandemic has made IT employees’ systems and data more prone to these attacks. Today, it has become essential for all businesses to adopt robust cyber security measures to prevent themselves from the losses caused by these threats. Businesses should leverage security testing to safeguard their IT systems, networks, apps, and infrastructure from possible threats and vulnerabilities.
Content
2. Why do businesses need security testing?
3. Recent cyber-attacks in 2022 depict the need for robust security testing
4. Different types of cyber threats businesses should know
5. What are the various security testing methods businesses can leverage?
What is security testing?

Security testing is a software testing technique where apps, systems, networks, infrastructure, etc., are tested for security threats and vulnerabilities. This testing method helps improve the security posture of businesses and protects them from all kinds of cyber threats. Further, it ensures that business systems, apps, and networks are free from security loopholes and vulnerabilities that hackers could otherwise exploit. Some of the basic concepts in security testing include Confidentiality, Integrity, Availability, Authenticity, Authorization, Non-repudiation, and Resilience.
Why do businesses need security testing?
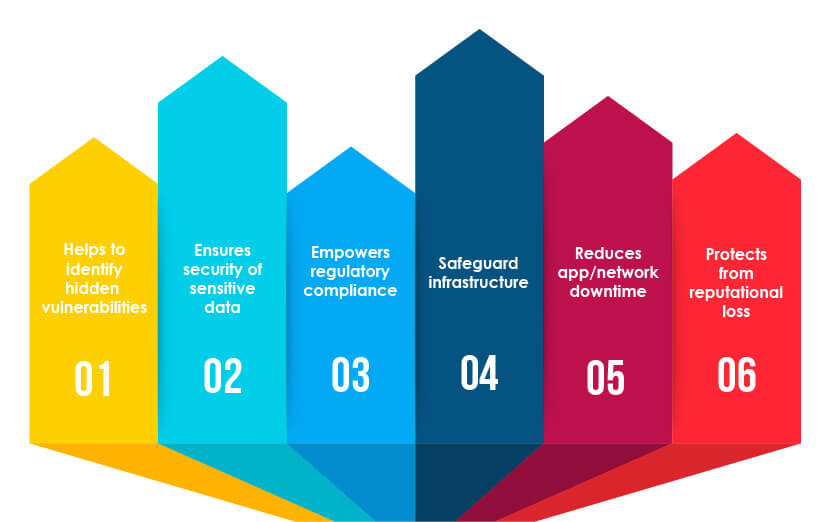
Helps to identify hidden vulnerabilities:
Security testing helps identify hidden issues or security loopholes in the software/app that, if left unidentified, can be exploited by hackers.
Ensures security of sensitive data:
Cyber security testing helps to keep customer and business-sensitive data secure from all risks.
Empowers regulatory compliance:
Businesses need to safeguard customer data and prevent data leakage. This testing method helps to ensure data safety and also allows businesses to fulfill regulatory compliances.
Safeguard infrastructure:
Security testing helps businesses safeguard their IT infrastructure from unknown threats and malicious attacks.
Reduces app/network downtime:
Cyber-attacks might lead to network or app downtime, which can stop the normal functioning of the business activities and might hamper customer experience (CX). Leveraging security testing protects from these attacks and helps reduce/eliminate app or network downtime.
Protects from reputational loss:
Cyber-attacks threaten the business’s reputation and might also affect its bottom line. Businesses can protect themselves from economic and reputational loss by leveraging security testing.
Recent cyber-attacks in 2022 depict the need for robust security testing

According to securityaffairs, on 24th March 2022, The Anonymous hacker collective claims to have hacked the Central Bank of Russia and accessed 35,000 documents. Anonymous claims that the stolen documents include Russia’s economic secrets. The attack on the central bank of a state could have major repercussions on its domestic politics.
According to novinkycz, on 22nd March 2022, Hacker group Anonymous released 10 GB of data from Swiss company Nestlé. This is the collective’s retaliation for continuing the company’s business in Russia.
According to Wikipedia, on 14th January 2022, a cyberattack took down more than a dozen of Ukraine’s government websites during the 2021–2022 Russo-Ukrainian crisis. According to Ukrainian officials, around 70 government websites, including the Ministry of Foreign Affairs, Cabinet of Ministers, and Security and Defense Council, were attacked.
Different types of cyber threats businesses should know
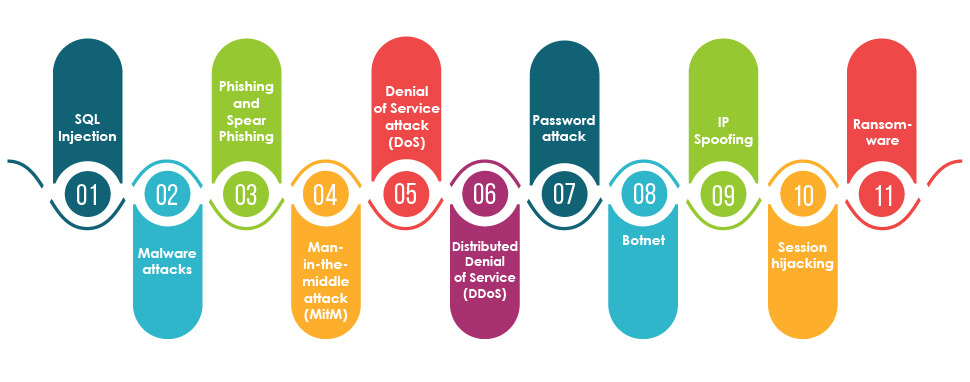
SQL Injection:
This technique involves injecting malicious SQL code into the entry field for hacking database-driven websites or websites that use dynamic SQL.
Malware attacks:
Hackers install malicious software on the victim’s system without consent in this cyberattack.
Phishing and Spear Phishing:
In this type of cyberattack, hackers send malicious emails that appear to be from genuine sources to gain personal information or influence victims to do something via these emails.
Man-in-the-middle attack (MitM):
In this cyberattack, a perpetrator intercepts the communication between client and server to either eavesdrop or impersonate someone.
Denial of Service attack (DoS):
In a DoS attack, the perpetrator shuts down the victim’s system or network to make it inaccessible to its intended users.
Distributed Denial of Service (DDoS):
In this Distributed Denial of Service attack, hackers flood the organization’s servers or networks with fake or bot users to crash the system’s normal functioning and interrupt the communication channel.
Password attack:
It is one of the most common types of cyberattacks where attackers use a mechanism to steal passwords by either looking around the person’s desk or using the sniffing technique.
Botnet:
It is a collection of malware-infected internet-connected devices that remains under the control of a single attacking party known as bot herders. It allows attackers to steal credentials saved on devices and gives them unauthorized access, leading to data theft and DDoS attacks.
IP Spoofing:
In this cyber attacking technique, the attacker modifies the IP address in the packet header. The receiving computer system thinks it is from a legitimate or trusted source.
Session hijacking:
In this attack, an attacker hijacks the user session. It usually starts when a user logs in to the application and ends when they log out.
Ransomware:
In this cyberattack, the attacker encrypts the victim’s file and demands a heavy amount of money or ransom to decrypt it.
Evidently, there are various types of cyber-attacks, and businesses should leverage robust security testing to protect themselves from these malicious attacks.
What are the various security testing methods businesses can leverage?
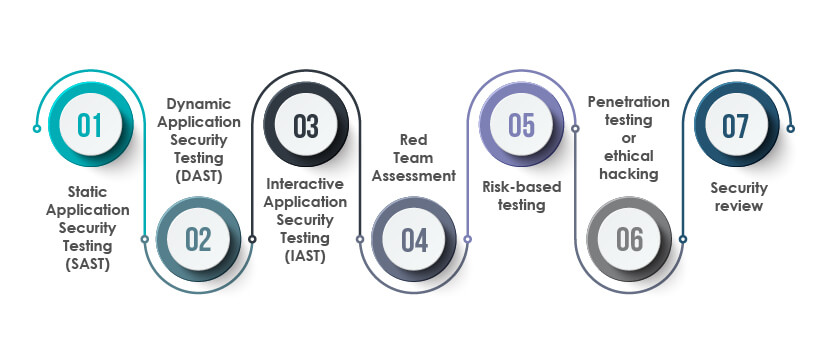
Static Application Security Testing (SAST):
SAST is a white box security testing technique where testers examine the source code to identify security defects. By using this security testing method, the security issues are identified and mitigated early
Dynamic Application Security Testing (DAST):
DAST is a black box testing technique that involves testing the application as it is running. This testing method helps identify security vulnerabilities that cyber-attackers could exploit if left unidentified.
Interactive Application Security Testing (IAST):
It is a cybersecurity testing technique that involves the usage of software instruments to assess applications in real-time. This testing method helps businesses identify and manage security risks and vulnerabilities while running web apps using dynamic testing techniques.
Red Team Assessment:
It is a broader aspect of penetration testing where the internal or external team of security experts simulate real-time attacks on the organization to determine how well an organization can defend itself from cyber attacks. Red team assessment helps to test an organization’s detection and response capabilities and also improves its security posture.
Risk-based testing:
It is the process of identifying and prioritizing potential risks associated with the software. The security testing teams prioritize the features and functions in software based on the risk of failure and its importance.
Penetration testing or ethical hacking:
In the Penetration testing method, a certified and authorized ethical hacker simulates cyberattacks to identify the security vulnerabilities in the software.
Security review: It is the process of safeguarding the entire DevOps environment by ensuring stringent security policies, strategies, best practices, procedures, and technology.
Important techniques used in security testing
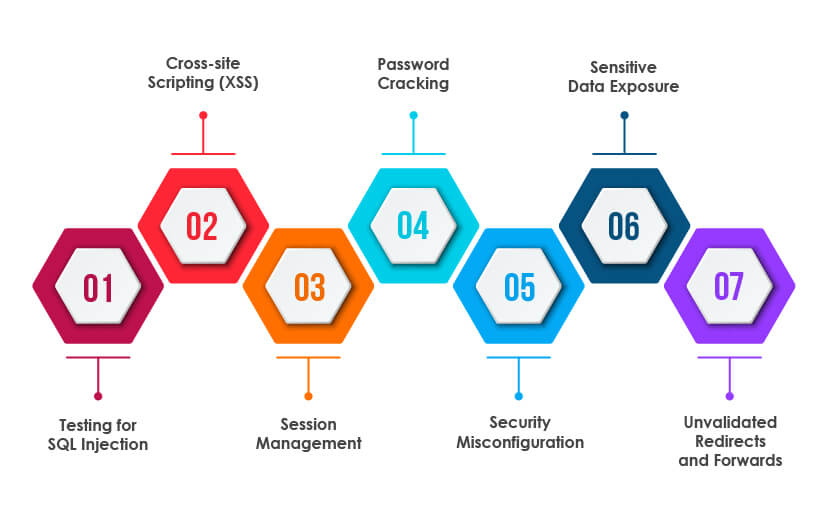
Testing for SQL Injection:
In this technique, testers check if it is possible to inject SQL queries into the input fields of the application without proper input validation.
Cross-site Scripting (XSS):
In this technique, testers check the web application for XSS to ensure that an application does not accept any HTML scripts. This attack happens when an attacker injects executable code within a single HTTP response.
Session Management:
Testers check the session expiration after a particular idle time after logging in and after the maximum lifetime. It also involves checking session duration and session cookie scope.
Password Cracking:
In this technique, testers try to crack the password to assess an application. They use commonly available user names, passwords, and open-source password cracking applications.
Security Misconfiguration:
It is one of the most common security flaws found in web applications due to weak or default passwords, out-of-date software, unnecessary features, and unprotected files or databases. Therefore, testers check all these aspects during the security testing.
Sensitive Data Exposure:
This issue happens when a web application fails to protect sensitive data and exposes it to end-user such as credit card/debit card information, contact information, health records, etc. Therefore, testers check the web applications to ensure that they do not expose sensitive data to the end-user.
Unvalidated Redirects and Forwards:
In this type of cyber-attacking technique, the hacker redirects or forwards the user to an untrusted website to steal information. Security testers check whether an application can stop redirection when it takes users to an untrusted link or website.
How is security testing performed in parallel to SDLC?

Security testing is a complex software testing process conducted either manually or with automation leveraging automation tools. It is best to start security testing in the early stages of SDLC, irrespective of the manual or automated approach. Below mentioned are ways in which security testing is done in parallel to SDLC:
Requirements gathering:
Testers perform security analysis and understand business needs and existing security posture during this stage.
Designing:
Once all the requirements are gathered, testers start security test planning.
Coding:
During the development or coding stage, testers perform white box testing or SAST and Software Composition Analysis.
Testing:
During the testing phase, testers perform Vulnerability Assessment & Penetration Testing using automated and manual methods.
Operations & Maintenance:
During this phase, testers perform impact analysis to find any other remaining security loopholes.
Role of security testing in the DevOps environment
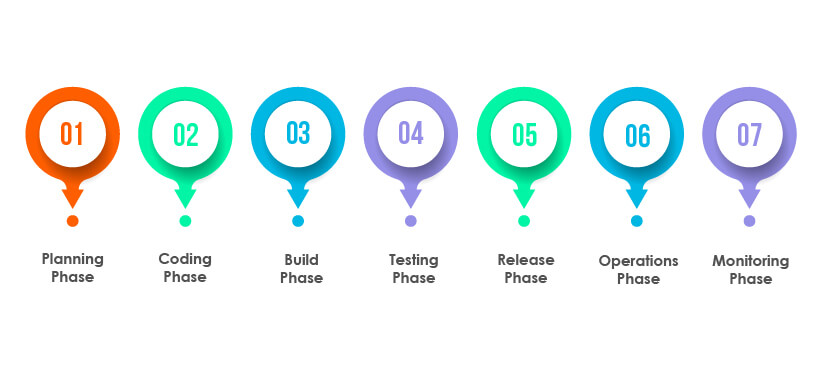
Security testing plays a vital role in the DevOps environment as it ensures continuous security checks throughout the DevOps CI/CD pipeline. Below mentioned are some ways in which security testing is integrated into the DevOps CI/CD pipeline:
Planning phase:
The DevSecOps team identifies the business’s security requirements and prepares security policies during this stage.
Coding phase:
At this stage, testers conduct in-depth code reviews to ensure the robustness of the software build.
Build phase:
During this stage, testers perform Static Application Security Testing (SAST) and dependency scanning.
Testing phase:
At this stage, testers execute Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and penetration testing to identify and remove vulnerabilities.
Release phase:
During this stage, the software is checked against all necessary guidelines, best practices, policies, and protocols. Continuous testing is ensured to remove all bugs.
Operations phase:
At this stage, Infrastructure as Code (IaC) and Secret management processes are implemented to ensure proper provisioning of infrastructure through code.
Monitoring phase:
At this stage, logging and alerting methods, threat intelligence methods, and vulnerability disclosure methods are used to ensure robust security.
Benefits of embedding security testing into the DevOps environment
• Helps testers to identify and rectify bugs early in the DevOps pipeline
• Delivers safer, secure, and resilient software
• Reduces expenses and losses
• Increases the delivery rate and ensures faster release of secured software
• Provides transparency from the start of the software development process
• Allows more rapid recovery in case a cyber-attack or security flaw is identified
• Ensures robust security checks and compliances in the delivery pipeline
• Provides the ability to respond to changes as and when they occur quickly
• Builds customer loyalty and uplifts the brand image
Who performs security testing?

Security testing involves various types of testers with varying roles. Depending on the complexity of IT infra, different testers are involved. Various types of testers involved in security testing are pen testers, security audit teams, security test engineers, cyber-security testing managers, etc.
Penetration testers, ethical hackers, or white hats are trained people who perform authorized simulated cyber-attacks on computer systems, networks, etc., to help businesses identify security vulnerabilities. Pen testers play a vital role in security testing by identifying security loopholes in IT infrastructure before a cyber-attacker finds and exploits them. Thus, penetration testers save businesses from monetary and reputational losses.
Best security testing practices to ensure robust cyber-security in 2022
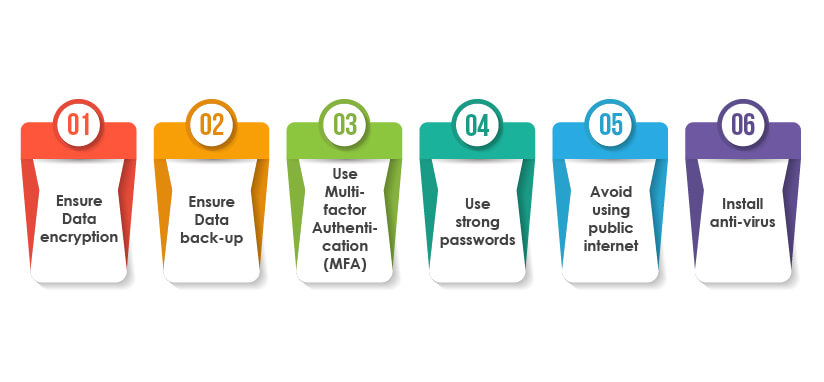
Ensure Data encryption:
Businesses should ensure end-to-end data encryption of sensitive and critical data. Data encryption converts the data into a secret code and reduces the risk of cyber threats, data destruction, or data tampering.
Ensure Data back-up:
Businesses need to keep their data back-up to ensure easy recovery if the data gets lost due to a cyberattack.
Use Multi-factor Authentication (MFA):
MFA is a security verification process that requires the user to provide two or more additional proofs of identity to access the account. This way, MFA adds a layer of security and safeguards businesses from cyber threats.
Use strong passwords:
It is necessary to use strong passwords with an appropriate combination of letters, alphabets, symbols, etc.
Avoid using public internet:
Systems connected to the public internet are more prone to cyber-attacks as hackers usually steal data or try to gain access to such systems.
Install anti-virus:
It is essential to install anti-virus to defend systems from cyber-attacks.
Upcoming Cyber-security threats and trends to look at in 2022
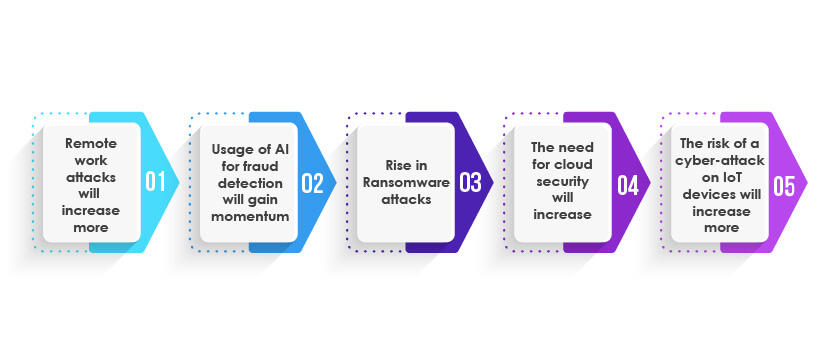
Remote work attacks will increase more:
The remote working culture that started with the COVID-19 pandemic is expected to continue for a long time as many organizations have adopted a permanent remote working policy. Due to this, the employees working from home are more prone to become victims of cyberattacks. According to Forbes, the cybersecurity threats that took advantage of this remote work dynamic will receive further attention.
Usage of AI for fraud detection will gain momentum:
In the upcoming years, it is expected that AI will be used more for fraud detection as it can analyze the data and find unusual patterns of cyber-attacks on the systems.According to Forbes, a shift to AI will help businesses meet the urgently needed gaps in the cybersecurity industry.
Rise in Ransomware attacks:
According to IBM, triple extortion ransomware is likely to rise in 2022. In this type of cyberattack, ransomware attack experienced by one business becomes an extortion threat for its business partner.
The need for cloud security will increase:
Today, businesses are rapidly adopting cloud solutions as it provides more benefits. However, cloud solutions are comparatively more secure than on-premise solutions as they have an added layer of security. Still, due to the advanced cyber-attacking techniques used by hackers, even cloud solutions are at risk of cyber threats today. According to Economic Times, cloud vulnerabilities are still a significant concern for many enterprises.
The risk of a cyber-attack on IoT devices will increase more:
The world is getting more connected with IoT devices and relies on heavy data, making it more prone to cyberattacks. According to IGT Solutions, the risk of cyber threats will increase in 2022 with more proliferation of IoT devices.
Security testing tools for businesses to leverage

Veracode:
It is a cloud-based security testing tool used to perform dynamic analysis (DAST), interactive analysis (IAST), static analysis (SAST), software composition analysis (SCA), and penetration testing.
Acunetix:
It is an end-to-end security testing tool that audits web applications by checking vulnerabilities like SQL Injection, Cross-site scripting, and other exploitable vulnerabilities. This tool comes with a suite of security testing tools: DeepScan Technology, Login Sequence Recorder (LSR), AcuMonitor, and AcuSensor.
Burp Suite Professional:
It is one of the widely used penetration testing and vulnerability scanning tools for web apps. This proxy-based tool evaluates the security of web-based applications and enables hands-on testing. It helps to find vulnerabilities faster and helps to save time and cost.
Microfocus Fortify:
It is a suite of automated security testing tools that support DevSecOps, Cloud transformation, software supply chain, Maturity at scale, Enterprise DAST, and CI/CD pipeline security. Various tools of this tool suite are: Fortify on Demand, Static Code Analyzer, Software Security Scanner, WebInspect, and Software Composition Analysis.
Conclusion
As businesses become more digital, there has been an increase in the number of cyber-attacks they face. It has become essential for digitally transforming businesses to ensure the robust security of apps, data, networks, systems, and infrastructure. It is necessary to adopt effective security measures such as strong passwords, multi-factor authentication, data encryption, etc., to protect businesses from cyber-attacks. Along with these measures, enterprises should leverage security testing methods like vulnerability scanning, pen testing, and ethical hacking to safeguard their systems, apps, networks, and IT infrastructure from possible cyber threats.
How can TestingXperts help?

TestingXperts (Tx), with its rich expertise in security testing, caters to businesses’ diversified security testing needs across industries. We have a large pool of Certified Ethical Hackers (CEH) that help businesses ensure their applications, networks, and servers are secure from all possible vulnerabilities and meet the stated security requirements like confidentiality, authorization, authentication, availability, and integrity. We are among the best security testing companies with expertise in assessing various applications for security threats. Tx teams ensure that your application is rigorously tested for all possible threats and vulnerabilities.
We primarily follow the OWASP (Open Web Security Project) guidelines in our security testing services along with PCI-DSS, HIPAA, SOX, WAHH, OSSTM, WASC, and NIST Standards as per the application-specific requirements.
Discover more
Get in Touch
Stay Updated
Subscribe for more info




