- What is Penetration Testing?
- What are the benefits with Pen Testing?
- What are the different types of Pen Testing?
- Who performs Pen Testing and what are the roles & responsibilities of Pen Testers
- Differences between Manual and Automated Penetration Testing
- What are the phases of Penetration Testing?
- What are the different approaches to Pen Testing?
- What are the important Penetration Testing Tools?
- Conclusion
What is Penetration Testing?
Pen testing or penetration testing is an ethical hacking process which involves assessing an application or an organization’s infrastructure for different types of vulnerabilities. This process of pen testing helps to exploit the various vulnerabilities within the system and the reasons for these vulnerabilities include certain misconfigurations, poorly designed architecture, insecure code, etc.
Thus, by performing pen testing, it eventually helps to identify vulnerabilities and the process delivers actionable reports that clearly explain each vulnerability, specifically how to exploit them along with how to fix them. Essentially, each of the vulnerability identified is given a specified rating with which the actionable remediation should be planned by the organizations.

Typically, a pen test is an ethical attack simulation that is performed to validate the effectiveness of security controls in a particular environment and highlights the possible vulnerabilities. This pen testing process involves the usage of various manual or automated techniques to simulate an attack on an organization’s information security (in a well informed environment to the organization so there is no actual data loss). The ethical hacking process could be run be from on company’s infrastructure or on employees within the same organization to test the security.
Primarily, businesses that store and access sensitive or private data such as banks, financial institutions, healthcare providers, etc. should adopt this form of testing to safeguard them from any possible vulnerabilities. Thus, businesses adopting pen testing tend to achieve many benefits by leveraging this method of testing.
What are the benefits with Pen Testing?
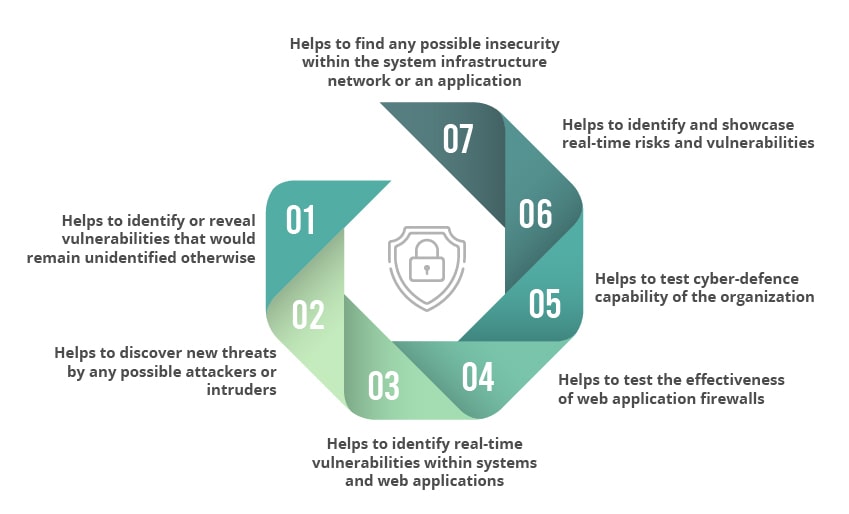
– Helps to identify vulnerabilities that would remain unidentified otherwise
– Helps to discover new threats by any possible attackers or intruders
– Helps to identify real-time vulnerabilities within systems and web applications
– Helps to test the effectiveness of web application firewalls
– Helps to test cyber-defence capability of the organization
– Helps to identify and showcase real-time risks and vulnerabilities
– Helps to find any possible insecurity within the system infrastructure network or an application
What are the different types of Pen Testing?
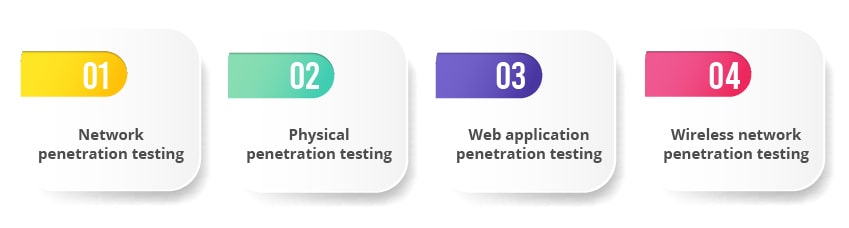
Network penetration testing:

In this type of pen testing, the physical structure of the system is checked primarily to identify risks in the network of the organization. In network Penetration testing, the penetration tester performs tests in the organization’s network and tries to find out flaws in the design, operation, or implementation of the respective company’s network. Various components of the organization such as computers, modems, remote access devices are all checked by the tester to exploit the possible vulnerabilities.
Physical penetration testing:

This method of physical penetration testing is done to simulate the real-world threats. The pen tester acts as a cyber-attacker and tries to break the physical barrier of security. This test is done to check for the vulnerabilities in physical controls like security cameras, lockers, barriers, sensors, etc.
Web application penetration testing:

This method of pen testing is done to check vulnerabilities or weaknesses within web-based applications. The web penetration testing looks out for any security issues that might occur due to insecure development due to design or code and identified potential vulnerabilities within websites and web apps. This type of penetration testing is most needed for online shopping websites, banking apps, and other eCommerce websites which deal with online transactions.
Wireless network penetration testing:

This form of pen testing is done to examine the connection between all devices like laptops, computers, tablets, smart-phones, etc, that are connected to the organization’s Wifi. This form of pen testing is done to prevent any data leakage that can happen while sharing data from one device to another device through the Wifi network.
Who performs Pen Testing and what are the roles & responsibilities of Pen Testers:

The penetration testing is conducted by pen testers who design and plan simulations and security assessments that are designed to probe any potential weaknesses within the system or IT infrastructure or web apps.
They are also responsible to document all the findings and deliver them to the clients or employees or to the organization. These pen testers perform the process of this testing either manually or by using certain set of automated tools and there are basic differences between these methods of testing.
Differences between Manual and Automated Penetration Testing
| – manual efforts are more needed to get better results for testing business logic vulnerabilities | – Automated tools can be used with very little human intervention, while manual testing cannot be performed for everything |
| – Manual penetration testing takes longer time | – Automated tools work faster and comparatively requires less time and perform the process with high speed |
| – When there is new vulnerability or exploit released, most of the automated tools will have to wait for next update while humans can learn new technique and implement it quickly | – This method of pen testing is best suited for testing targets with large number of pay loads |
| – With manual testing the false positives are less when compared to automated testing | – With automated pen testing, the false positives are comparatively more |
What are the phases of Penetration Testing?
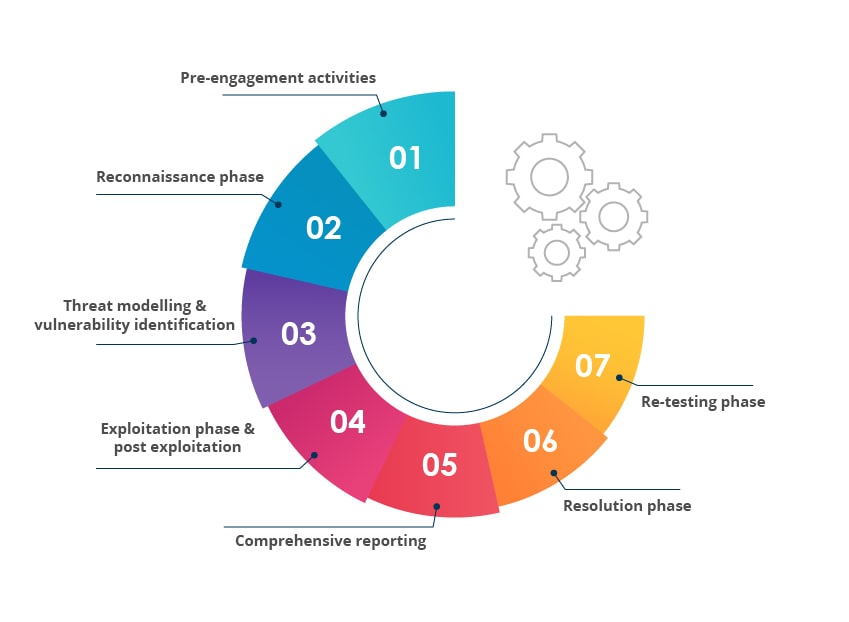
– Pre-engagement activities
– Reconnaissance phase
– Threat modelling & vulnerability identification
– Exploitation phase & post exploitation
– Comprehensive reporting
– Resolution phase
– Re-testing phase
What are the different approaches to Pen Testing?

Depending up on the level of information that is available to the pen tester, there are three types of approaches to pen testing.
Black box:

Black box pen testing is also commonly known as external penetration testing. In this approach, the pen tester has no information about the IT infrastructure of the organization. This process appears to be more like simulation of real-world cyber-attack to check the vulnerabilities in the system.
Specifically, in this method, the pen testers act as cyber-attackers and try to exploit the vulnerabilities that exist in the system. This process usually takes a lot of time and can take even up to six weeks to complete.
White box:

White box penetration testing is also known as internal penetration testing, clear box, or even known as glass box penetration testing. In this approach of pen testing, the pen tester is provided with the complete information of the IT Infrastructure, source code, and environment.
It is a much detailed and in-depth type of pen test done wherein every area is checked such as the quality of code and the basic design of the application. Moreover, this type of pen testing approach usually takes two to three weeks to get completed.
Gray box:

In this approach of penetration testing, the pen tester is provided with partial information of IT infrastructure, and code structure. It is a more focused approach as the pen tester has partial knowledge or access to internal network or web application and can focus some effort on exploiting the possible vulnerabilities which typically saves a lot of time and cost.
What are the important Penetration Testing Tools?
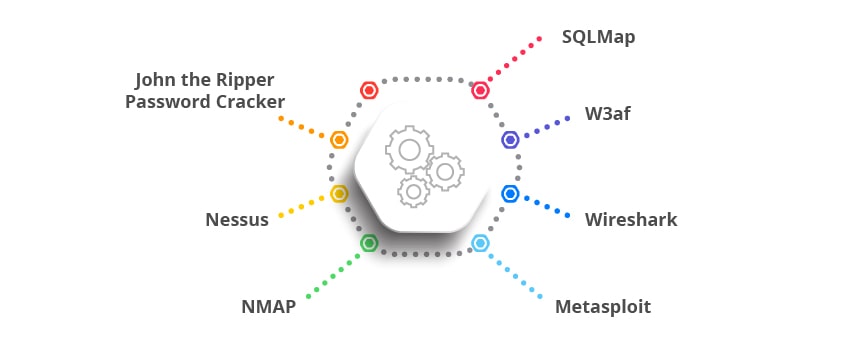
SQLMap:
It is an open-source tool used in penetration testing to detect flaws with an SQL Injection into an application. It automates the process of penetration testing and this tool supports many platforms like Windows, Linux, Mac, etc.
W3af:
The web application attack and audit framework (W3af) is used to find any weaknesses or vulnerabilities in web-based applications. It is used to remove threats such as DNS, cache poisoning, cookie handling, proxy support, etc.
Wireshark:
This is an open source tool and is available for many operating systems such as Windows, Solaris, Linux, etc. With this tool, the pen tester one can easily capture and interpret network packets. This tool provides both offline analysis and live-capture options.
Metasploit:
It is one of the most commonly used penetration testing tools in the world. It is an open source tool that allows the user to verify and manage security assessments, helps in identifying flaws, setting up a defence, etc.
NMAP:
It is also called network mapper and is used to find the gaps or issues in the network environment of the organization. This tool is also used for auditing purposes.
Nessus:
It is one of the most trusted pen testing tools by many companies across the world. It helps in scanning IP addresses, websites, and completing sensitive data searches.
John the Ripper Password Cracker:
It is an open-source software which is used to detect vulnerabilities in passwords. This tool automatically identifies different password hashes and finds issues with the passwords within the database. Its pro version is available for Mac, Linux, Hash Suite, and Hash Suite Droid.
Conclusion:
Penetration testing is an effective testing process that helps to uncover the critical security issues of your system to check for exploitable vulnerabilities to their IT Infrastructure, or web applications. As cyber threats continue to increase, it has become essential for companies to keep their IT infrastructure, web apps and systems safe and secure from any possible threats and vulnerabilities. Therefore, penetration testing has become so important in today’s digital world with rampant cyber-attacks on the go.
TestingXperts with its team of highly skilled security and pen testers ensures the best pen testing services to give you the complete benefit and helps to identify any possible vulnerabilities within your systems or IT infrastructure or web apps. Get in touch with our security testing experts today.
Discover more
Get in Touch
Stay Updated
Subscribe for more info